P2P Streaming 2020

The benefits from P2P Streaming:
- It can drastically reduce the number of bits that a CDN has to deliver.
- It can source bits from viewers closer to the end user, which takes much of strain off the Internet architecture.
But P2P is facing the following challenges:
- Users need client-side software or plugin, which kept P2P from reaching the mass adoption.
- Users fear of viruses and malware and worry that the P2P client will slow down their Internet connections.
- Unlike downloading static files via P2P, but for streaming requires to capture bits from multiple seeds and put them in the correct order. It is somewhat more complicated than simple file sharing.
- P2P present one of the core issues in the network neutrality controversy. Because P2P file-sharing consists of relatively heavy bandwidth usage due to ongoing file transfers and swarm/network coordination packets, ISPs have been known to throttle P2P file-sharing traffic.
In P2P, P2P applications use various tricks to punch holes in firewalls so that they can exchange packets with their counterpart as directly as possible. The firewall (router) translates the PC's local network address (private) to the public IP address via NAT. This means an attacker cannot directly address the PC from the outside - connections have to be established from the inside (out bound). This poses serious problem when two computers behind NAT firewalls (on private networks) want to talk directly to each other via VoIP. However, whichever party calls the other, the recipient's firewall will decline the apparent attack (inbound) and will simply discard the data packets. The recipient's phone won't be ringing.
In other words, the current address architecture of Internet is suitable only for client/server communication such as when the client is on a private network and the server is in the public network. However, the architecture makes it difficult for two nodes on different private networks to connect each other directly, which is the core of the p2p communication protocols used in applications such as teleconferencing, online gaming, and streaming.
Let's start from the definition of a session. For TCP/UDP, a session endpoint is a pair of IP address and port number, and a particular session is uniquely identified by its two session endpoints. In other words, a session is effectively identified by the 4-tuple (local IP, local port, remote IP, remote port). The direction of a session is normally the flow direction of the packet that initiates the session: for TCP, the initial SYN packet for TCP, or for UDP, the first user datagram.
The most common type of NAT (Network Address Translation) (see How NAT Works, CISCO) is outbound NAT. It provides an asymmetric bridge between a private network and a public network. Outbound NAT by default allows only outbound sessions to traverse the NAT. In other words, incoming packets are dropped unless the NAT identifies them as being part of an existing session initiated from within the private network. Outbound NAT conflicts with peer-to-peer protocols because when both peers desiring to communicate are on the private network side of two different NATs, whichever peer tries to initiate a session, the other peer's NAT rejects it. NAT traversal entails making P2P sessions look like outbound sessions to both NATs.
Hole punching is a technique used to establish communications between two private (behind firewalls) hosts. The technique is used in applications such as online gaming, P2P, and VoIP. The two clients establish a connection with a server that maintains public and private address information for them. Because each client initiated the request to the server, the server knows their public/private IP addresses and public/private port numbers assigned for that session, which it shares one to the other. The valid port numbers make the firewalls to accept the incoming packets from each side.
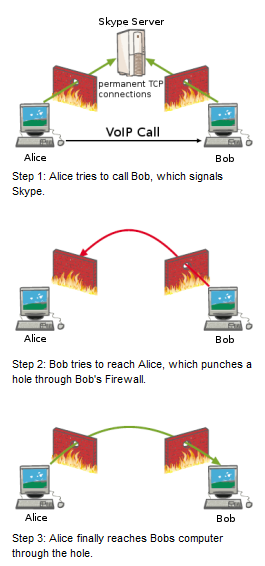
Picture from How Skype Co get round firewalls.
UDP hole punching establishes connectivity between two hosts communicating across one or more NATs. It typically implements the STUN method or Interactive Connectivity Establishment (ICE) to determine the public address of the NAT.
For more information, Peers Behind Different NATs.
Or visit https://wiki.theory.org/BitTorrentSpecification
Another P2P application, Skype, check this pdf:
An Analysis of the Skype Peer-to-Peer Internet Telephony
Protocol by Salman A. Baset and Henning Schulzrinne(pdf)
Skype turned 10 years old today. After disrupting the telecommunications industry, Skype is facing an uncertain future and increased competition. It is increasingly being assimilated into Microsoft and its enterprise communications business. Will the brand last another 10 years? I am not so sure.
...
Aug 30, 2013 - GigaOm
BitTorrent is looking for webcasters to test P2P live streaming - BitTorrent Inc. is reaching out to broadcasters and webcasters, asking them to test its live streaming technology. The company posted an invitation to join the ongoing test program of BitTorrent Live on its blog - Nov. 21, 2012 from GigaOm
BitTorrent's New Trick: Letting You Send Terabyte-Sized Email Attachments - BitTorrent Inc. - Feb 15, 2013
Not too long ago, BitTorrent launched a little project called Sync, which provides practically unlimited "cloud" storage. Now the professional sharers are rolling out yet another service called "SoShare" which promises to let you easily send huge files to friends and coworkers with little to no hassle. Up to a whole terabyte at the click of a button.
Like Sync, SoShare pulls its power from that BitTorrent technology we all know and love, and spins it out into yet another application. With SoShare, you simply upload the files you want to send using the service's web-client, and then specify the email addresses of the folks you'd like to send it too. Then, presto, the recipients get a link in their email and can start downloading right away, without setting up an account of their own. All they need is the SoShare plugin. And if you really want to share the love, you can get a public download link and put it anywhere you want.
Ph.D. / Golden Gate Ave, San Francisco / Seoul National Univ / Carnegie Mellon / UC Berkeley / DevOps / Deep Learning / Visualization