Django with Kubenetes III: Gunicorn and Nginx with Ansible / AWS

- Ansible:
We must configure the PPA on our system to install the latest version of ansible. To manage the repositories that we install software from various PPA (Personal Package Archives). It allow us to upload Ubuntu source packages to be built and published as an apt repository by Launchpad. Type the following apt-get command or apt command:
$ sudo apt update $ sudo apt upgrade $ sudo apt install software-properties-common
Add ppa:ansible/ansible to your system's Software Source:
$ sudo apt-add-repository ppa:ansible/ansible $ sudo apt update $ sudo apt install ansible $ ansible --version ansible 2.6.5 config file = /etc/ansible/ansible.cfg configured module search path = ['/home/k/.ansible/plugins/modules', '/usr/share/ansible/plugins/modules'] ansible python module location = /home/k/.local/lib/python3.5/site-packages/ansible executable location = /home/k/.local/bin/ansible python version = 3.5.2 (default, Nov 23 2017, 16:37:01) [GCC 5.4.0 20160609]
For the Ansible to use Python3, we may need to set:
$ export ANSIBLE_PYTHON_INTERPRETER=/usr/bin/python3
- boto is a Python package that provides interfaces to Amazon Web Services.
$ python Python 3.5.2 ... >>> import boto >>>
To authenticate an AWS account, we need to add our access key id and secret access key to env-vars:
$ source env-vars
Ansible uses a combination of a hosts file and a group_vars directory to pull variables per host group and run Ansible plays/tasks against hosts.
group_vars/all is used to set variables that will be used for every host that Ansible is ran against.
In our hosts file, we're defining the common vars for the all group:
[all:vars] home_dir="/home/ubuntu" ansible_user=ubuntu apt_update=true postgresql_version=9.3 db_user=postgres gunicorn_group=webapps [test-servers] test-alpha ansible_host: 34.228.81.21
Note that we also defined variables under group_vars as all and test_servers.
Let's try to connect to the instance via Ansible:
$ ansible -i hosts all -m ping -u ubuntu
18.212.85.33 | SUCCESS => {
"changed": false,
"ping": "pong"
}
- setup.yml - this playbook will setup and deploy a project to a server. To run this playbook:
--- - name: Prepare a new instance for deployment hosts: test-servers gather_facts: no vars: - apt_update: yes roles: - { role: base, become: yes } - { role: postgresql, become: yes }In the playbook, we defined variables in vars as "apt-update: yes". It runs the roles: role: base, role: postgresql
.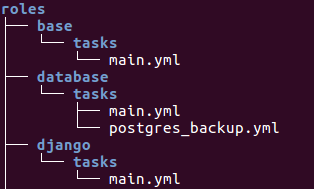
Roles must include at least one of these directories, however it is perfectly fine to exclude any which are not being used. When in use, each directory must contain a main.yml file, which contains the relevant content:
- tasks - contains the main list of tasks to be executed by the role.
- handlers - contains handlers, which may be used by this role or even anywhere outside this role.
- defaults - default variables for the role (see Variables for more information).
- vars - other variables for the role (see Variables for more information).
- files - contains files which can be deployed via this role.
- templates - contains templates which can be deployed via this role.
- meta - defines some meta data for this role. See below for more details.
Roles are ways of automatically loading certain vars_files, tasks, and handlers based on a known file structure. Roles expect files to be in certain directory names.
Run the playbook:
$ ansible-playbook -i hosts setup.yml
The role 'postgresql' authenticates user postgres with trust.
- status.yml - this playbook checks the status of all servers
$ ansible-playbook -i hosts status.yml
- launch_instance.yml:
This playbook provides the AWS account access key and secret in the env variables AWS_ACCESS_KEY_ID and AWS_ACCESS_SECRET_KEY. When both these conditions are satisfied, run this command:
$ ansible-playbook -i hosts.local launch_instance.yml
This playbook takes the following variables: key_name, instance_type, security_group, image, region, iam_role_name. Each of these variables can be overridden on the command line with --extra-vars. This playbook will launch an instance for the AWS account, assigned to a role with name 'iam_role_name', instance type 'instance_type' and so on.
While it is possible to write a playbook in one very large file, eventually we'll want to reuse files and start to organize things.
At a basic level, including task files allows you to break up bits of configuration policy into smaller files. Task includes pull in tasks from other files. Since handlers are tasks too, you can also include handler files from the 'handlers:' section.
The following roles are available for preparing a complete stack for a Django application with PostgreSQL database:
- base - installs required packages
- postgresql - installs and configures Postgres to allow access to db user
- django - creates virtual environment, install requirements, create gunicorn config, etc.
- nginx - creates Nginx configurations and start server
Ph.D. / Golden Gate Ave, San Francisco / Seoul National Univ / Carnegie Mellon / UC Berkeley / DevOps / Deep Learning / Visualization