AWS - Lambda and SNS : cross account
- Account A (047109936880), profile = khong-aol
- Account B (526262051452), profile = K
Account A
From account A (047109936880), create the source Amazon SNS topic:
$ aws sns create-topic --name lambda-x-account --profile kong-aol
{
"TopicArn": "arn:aws:sns:us-east-1:047109936880:lambda-x-account"
}
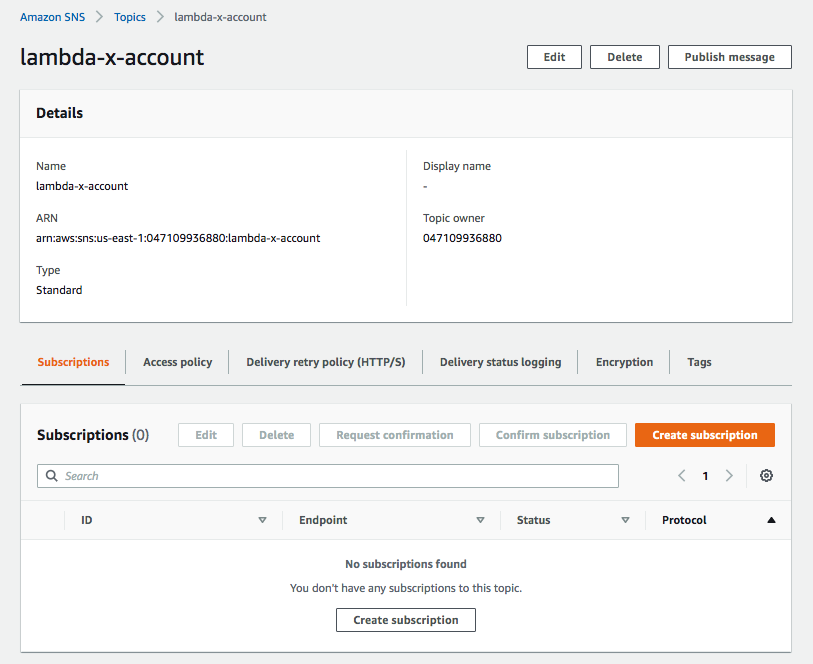
Account B
Creating the execution role
>From account B (526262051452), create the execution role that gives our function permission to access AWS resources.
To create an execution role
- Open the roles page in the IAM console.
- Choose Create role.
- Create a role with the following properties.
- Trusted entity – AWS Lambda.
- Permissions – AWSLambdaBasicExecutionRole.
- Role name – lambda-sns-role.
The AWSLambdaBasicExecutionRole policy has the permissions that the function needs to write logs to CloudWatch Logs.
Creating a Lambda function
From account B (526262051452), create the function that processes events from Amazon SNS. The following example code receives an Amazon SNS event input and processes the messages that it contains. Note that the code writes some of the incoming event data to CloudWatch Logs.
lambda_function.py:
from __future__ import print_function
import json
print('Loading function')
def lambda_handler(event, context):
#print("Received event: " + json.dumps(event, indent=2))
message = event['Records'][0]['Sns']['Message']
print("From SNS: " + message)
return message
$ zip function.zip lambda_function.py adding: lambda_function.py (deflated 35%)
$ aws lambda create-function --function-name SNS-X-Account \
--zip-file fileb://function.zip --handler lambda_function.lambda_handler \
--role arn:aws:iam::526262051452:role/lambda-sns-role \
--region us-east-1 --profile K --runtime python3.8
{
"FunctionName": "SNS-X-Account",
"FunctionArn": "arn:aws:lambda:us-east-1:526262051452:function:SNS-X-Account",
"Runtime": "python3.8",
"Role": "arn:aws:iam::526262051452:role/lambda-sns-role",
"Handler": "lambda_function.lambda_handler",
"CodeSize": 368,
"Description": "",
"Timeout": 3,
"MemorySize": 128,
"LastModified": "2021-06-10T16:49:01.092+0000",
"CodeSha256": "C5v96GAxpEmPf2XYQlLEiDvIRq0mpkzfMAE2FAasGYs=",
"Version": "$LATEST",
"TracingConfig": {
"Mode": "PassThrough"
},
"RevisionId": "92250b66-498e-41c7-bbee-50a3b7980c48",
"State": "Active",
"LastUpdateStatus": "Successful",
"PackageType": "Zip"
}
Set up cross-account permissions
From account A (047109936880), grant permission to account B (526262051452) to subscribe to the topic:
$ aws sns add-permission --label lambda-access --aws-account-id 526262051452 \ --topic-arn arn:aws:sns:us-east-1:047109936880:lambda-x-account \ --action-name Subscribe ListSubscriptionsByTopic --profile khong-aol
So, the access policy of the topic (accountA) looks like this:
{
"Version": "2008-10-17",
"Id": "__default_policy_ID",
"Statement": [
{
"Sid": "__default_statement_ID",
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": [
"SNS:GetTopicAttributes",
"SNS:SetTopicAttributes",
"SNS:AddPermission",
"SNS:RemovePermission",
"SNS:DeleteTopic",
"SNS:Subscribe",
"SNS:ListSubscriptionsByTopic",
"SNS:Publish",
"SNS:Receive"
],
"Resource": "arn:aws:sns:us-east-1:047109936880:lambda-x-account",
"Condition": {
"StringEquals": {
"AWS:SourceOwner": "047109936880"
}
}
},
{
"Sid": "lambda-access",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::526262051452:root"
},
"Action": [
"SNS:Subscribe",
"SNS:ListSubscriptionsByTopic"
],
"Resource": "arn:aws:sns:us-east-1:047109936880:lambda-x-account"
}
]
}
From account B (526262051452), add the Lambda permission to allow invocation from Amazon SNS:
$ aws lambda add-permission --function-name SNS-X-Account \
--source-arn arn:aws:sns:us-east-1:047109936880:lambda-x-account \
--statement-id sns-x-account --action "lambda:InvokeFunction" \
--principal sns.amazonaws.com --profile K
{
"Statement": "{\"Sid\":\"sns-x-account\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":\"sns.amazonaws.com\"},\"Action\":\"lambda:InvokeFunction\",\"Resource\":\"arn:aws:lambda:us-east-1:526262051452:function:SNS-X-Account\",\"Condition\":{\"ArnLike\":{\"AWS:SourceArn\":\"arn:aws:sns:us-east-1:047109936880:lambda-x-account\"}}}"
}
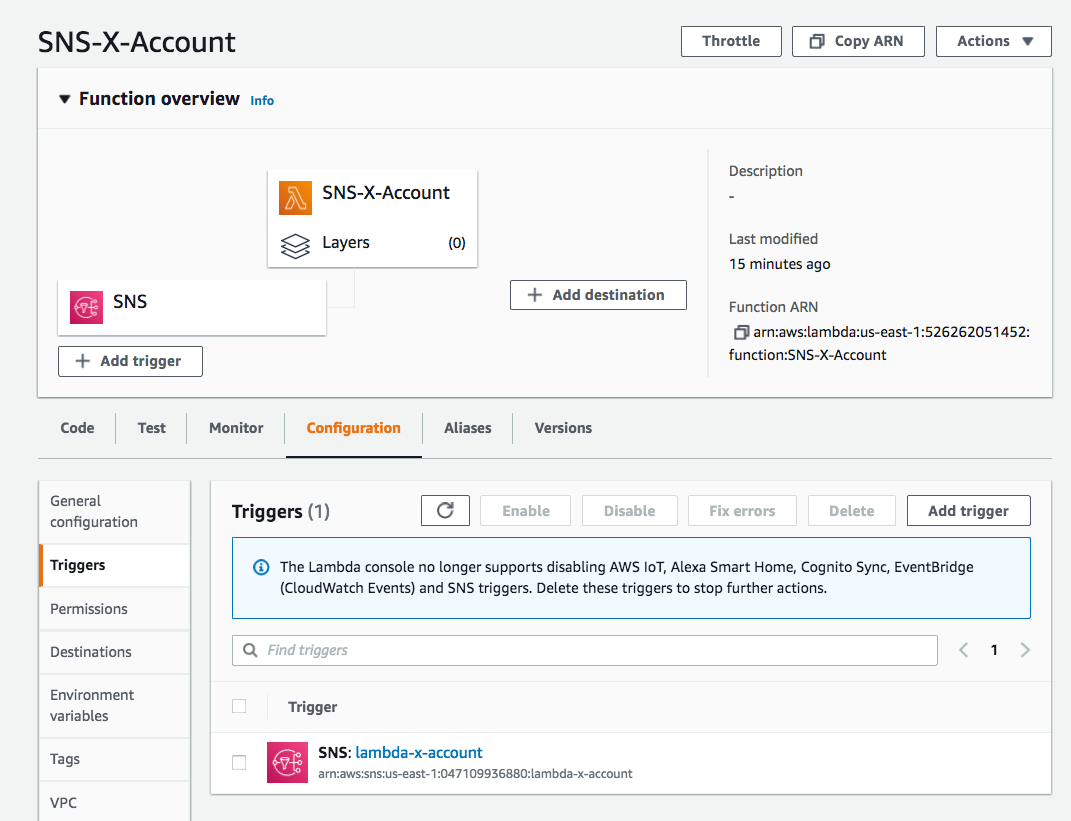
The invocation (triggers) on the Lambda function of accountB has been updated:
Creating a subscription
From account B, subscribe the Lambda function to the topic. When a message is sent to the lambda-x-account topic in account A (047109936880), Amazon SNS invokes the SNS-X-Account function in account B (526262051452):
$ aws sns subscribe --protocol lambda \
--topic-arn arn:aws:sns:us-east-1:047109936880:lambda-x-account \
--notification-endpoint arn:aws:lambda:us-east-1:526262051452:function:SNS-X-Account \
--profile K
{
"SubscriptionArn": "arn:aws:sns:us-east-1:047109936880:lambda-x-account:b1be7baa-4f5e-4f4c-a2e5-fa826bde0612"
}
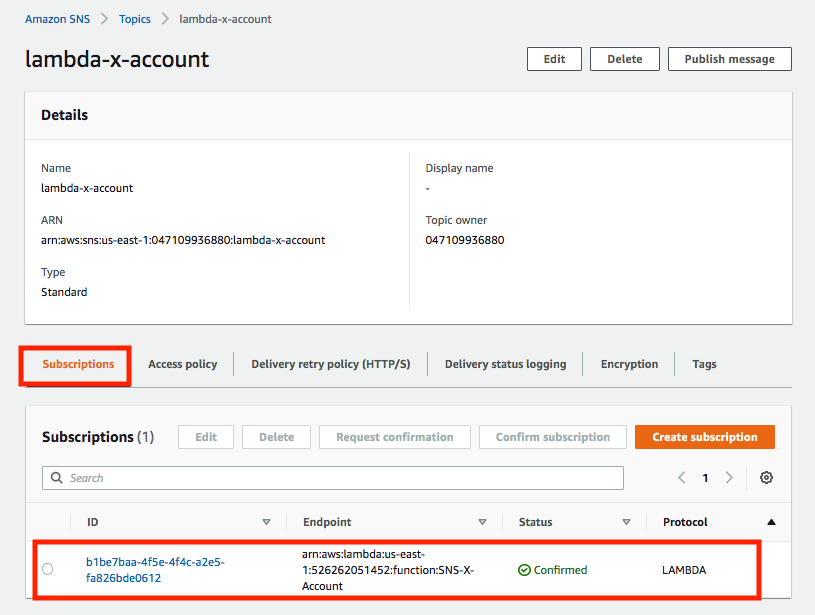
Now on the topic of accountA, we can see a new subscription has been created:
Testing the subscription
From account A (047109936880), test the subscription. Type Hello World into a text file and save it as message.txt. Then run the following command:
$ aws sns publish --message file://message.txt --subject Test \
--topic-arn arn:aws:sns:us-east-1:047109936880:lambda-x-account \
--profile khong-aol
{
"MessageId": "9825b3d7-cd86-5b8d-b4db-eaeb97b80248"
}
This will return a message id with a unique identifier, indicating the message has been accepted by the Amazon SNS service. Amazon SNS will then attempt to deliver it to the topic's subscribers. Alternatively, we could supply a JSON string directly to the message parameter, but using a text file allows for line breaks in the message.
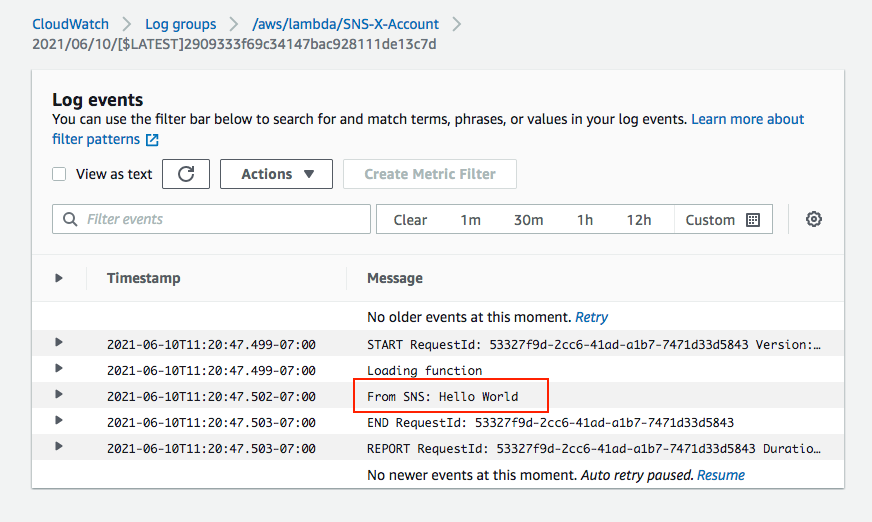
We can see our lambda has been triggered by the SNS:
This post is based on Tutorial: Using AWS Lambda with Amazon Simple Notification Service
AWS (Amazon Web Services)
- AWS : EKS (Elastic Container Service for Kubernetes)
- AWS : Creating a snapshot (cloning an image)
- AWS : Attaching Amazon EBS volume to an instance
- AWS : Adding swap space to an attached volume via mkswap and swapon
- AWS : Creating an EC2 instance and attaching Amazon EBS volume to the instance using Python boto module with User data
- AWS : Creating an instance to a new region by copying an AMI
- AWS : S3 (Simple Storage Service) 1
- AWS : S3 (Simple Storage Service) 2 - Creating and Deleting a Bucket
- AWS : S3 (Simple Storage Service) 3 - Bucket Versioning
- AWS : S3 (Simple Storage Service) 4 - Uploading a large file
- AWS : S3 (Simple Storage Service) 5 - Uploading folders/files recursively
- AWS : S3 (Simple Storage Service) 6 - Bucket Policy for File/Folder View/Download
- AWS : S3 (Simple Storage Service) 7 - How to Copy or Move Objects from one region to another
- AWS : S3 (Simple Storage Service) 8 - Archiving S3 Data to Glacier
- AWS : Creating a CloudFront distribution with an Amazon S3 origin
- AWS : Creating VPC with CloudFormation
- AWS : WAF (Web Application Firewall) with preconfigured CloudFormation template and Web ACL for CloudFront distribution
- AWS : CloudWatch & Logs with Lambda Function / S3
- AWS : Lambda Serverless Computing with EC2, CloudWatch Alarm, SNS
- AWS : Lambda and SNS - cross account
- AWS : CLI (Command Line Interface)
- AWS : CLI (ECS with ALB & autoscaling)
- AWS : ECS with cloudformation and json task definition
- AWS Application Load Balancer (ALB) and ECS with Flask app
- AWS : Load Balancing with HAProxy (High Availability Proxy)
- AWS : VirtualBox on EC2
- AWS : NTP setup on EC2
- AWS: jq with AWS
- AWS & OpenSSL : Creating / Installing a Server SSL Certificate
- AWS : OpenVPN Access Server 2 Install
- AWS : VPC (Virtual Private Cloud) 1 - netmask, subnets, default gateway, and CIDR
- AWS : VPC (Virtual Private Cloud) 2 - VPC Wizard
- AWS : VPC (Virtual Private Cloud) 3 - VPC Wizard with NAT
- DevOps / Sys Admin Q & A (VI) - AWS VPC setup (public/private subnets with NAT)
- AWS - OpenVPN Protocols : PPTP, L2TP/IPsec, and OpenVPN
- AWS : Autoscaling group (ASG)
- AWS : Setting up Autoscaling Alarms and Notifications via CLI and Cloudformation
- AWS : Adding a SSH User Account on Linux Instance
- AWS : Windows Servers - Remote Desktop Connections using RDP
- AWS : Scheduled stopping and starting an instance - python & cron
- AWS : Detecting stopped instance and sending an alert email using Mandrill smtp
- AWS : Elastic Beanstalk with NodeJS
- AWS : Elastic Beanstalk Inplace/Rolling Blue/Green Deploy
- AWS : Identity and Access Management (IAM) Roles for Amazon EC2
- AWS : Identity and Access Management (IAM) Policies, sts AssumeRole, and delegate access across AWS accounts
- AWS : Identity and Access Management (IAM) sts assume role via aws cli2
- AWS : Creating IAM Roles and associating them with EC2 Instances in CloudFormation
- AWS Identity and Access Management (IAM) Roles, SSO(Single Sign On), SAML(Security Assertion Markup Language), IdP(identity provider), STS(Security Token Service), and ADFS(Active Directory Federation Services)
- AWS : Amazon Route 53
- AWS : Amazon Route 53 - DNS (Domain Name Server) setup
- AWS : Amazon Route 53 - subdomain setup and virtual host on Nginx
- AWS Amazon Route 53 : Private Hosted Zone
- AWS : SNS (Simple Notification Service) example with ELB and CloudWatch
- AWS : Lambda with AWS CloudTrail
- AWS : SQS (Simple Queue Service) with NodeJS and AWS SDK
- AWS : Redshift data warehouse
- AWS : CloudFormation
- AWS : CloudFormation Bootstrap UserData/Metadata
- AWS : CloudFormation - Creating an ASG with rolling update
- AWS : Cloudformation Cross-stack reference
- AWS : OpsWorks
- AWS : Network Load Balancer (NLB) with Autoscaling group (ASG)
- AWS CodeDeploy : Deploy an Application from GitHub
- AWS EC2 Container Service (ECS)
- AWS EC2 Container Service (ECS) II
- AWS Hello World Lambda Function
- AWS Lambda Function Q & A
- AWS Node.js Lambda Function & API Gateway
- AWS API Gateway endpoint invoking Lambda function
- AWS API Gateway invoking Lambda function with Terraform
- AWS API Gateway invoking Lambda function with Terraform - Lambda Container
- Amazon Kinesis Streams
- AWS: Kinesis Data Firehose with Lambda and ElasticSearch
- Amazon DynamoDB
- Amazon DynamoDB with Lambda and CloudWatch
- Loading DynamoDB stream to AWS Elasticsearch service with Lambda
- Amazon ML (Machine Learning)
- Simple Systems Manager (SSM)
- AWS : RDS Connecting to a DB Instance Running the SQL Server Database Engine
- AWS : RDS Importing and Exporting SQL Server Data
- AWS : RDS PostgreSQL & pgAdmin III
- AWS : RDS PostgreSQL 2 - Creating/Deleting a Table
- AWS : MySQL Replication : Master-slave
- AWS : MySQL backup & restore
- AWS RDS : Cross-Region Read Replicas for MySQL and Snapshots for PostgreSQL
- AWS : Restoring Postgres on EC2 instance from S3 backup
- AWS : Q & A
- AWS : Security
- AWS : Security groups vs. network ACLs
- AWS : Scaling-Up
- AWS : Networking
- AWS : Single Sign-on (SSO) with Okta
- AWS : JIT (Just-in-Time) with Okta
Ph.D. / Golden Gate Ave, San Francisco / Seoul National Univ / Carnegie Mellon / UC Berkeley / DevOps / Deep Learning / Visualization