Puppet Express

Puppet
In this chapter, we can get quick view of puppet.
We need to machines to make things work. We may want to setup two ec2 instances to play with puppet: puppet master & puppet agent, and actually we'll use aws instances.
Let's install puppet master:
$ sudo apt-get install puppetmaster
To start it:
$ sudo service puppetmaster start
Let's install puppet client:
$ sudo apt-get install puppet
To start puppet agent:
$ sudo service puppet start
To start the client at boot, we may want to edit /etc/default/puppet:
# Defaults for puppet - sourced by /etc/init.d/puppet # Start puppet at boot time START=yes # Startup options DAEMON_OPTS=""
When the puppet client starts, it sends a request for signing it's cert to master:
ubuntu@ip-172-31-35-27:~$ sudo puppet cert list "agent-node.us-west-1.compute.internal" (SHA256) A7:9D:EF:EF:14:84:2F:C8:6C:3E:BB:18:44:B0:... ubuntu@ip-172-31-35-27:~$
Or we explicitly request master's sign:
ubuntu@agent-node:~$ sudo puppet agent -t Info: Creating a new SSL key for agent-node.us-west-1.compute.internal Info: csr_attributes file loading from /etc/puppet/csr_attributes.yaml Info: Creating a new SSL certificate request for agent-node.us-west-1.compute.internal Info: Certificate Request fingerprint (SHA256): A7:9D:EF:EF:14:84:2F:C8:6C:3E:BB:18:44:B0:... Exiting; no certificate found and waitforcert is disabled
From the output, we can see the client that just started. Puppet master should sign the cert to authorize communication between the client and the master:
ubuntu@ip-172-31-35-27:~$ sudo puppet cert sign agent-node.us-west-1.compute.internal Notice: Signed certificate request for agent-node.us-west-1.compute.internal Notice: Removing file Puppet::SSL::CertificateRequest agent-node.us-west-1.compute.internal at '/var/lib/puppet/ssl/ca/requests/agent-node.us-west-1.compute.internal.pem'
We can list all singed cert:
ubuntu@ip-172-31-35-27:~$ sudo puppet cert list -all + "agent-node.us-west-1.compute.internal" (SHA256) 99:8F:42:62:88:C0:77:E3:96:0F:37:E8:FA:AE:DB:... + "ip-172-31-35-27.us-west-1.compute.internal" (SHA1) E3:A1:B2:AB:D0:0E:20:45:76:03:12:3D:24:30:EB:31:EF:6C:6B:B7 (alt names: "DNS:ip-172-31-35-27.us-west-1.compute.internal", "DNS:puppet", "DNS:puppet.us-west-1.compute.internal") + "ip-172-31-35-28.us-west-1.compute.internal" (SHA256) DB:C9:25:A9:E7:71:44:75:E6:E2:5E:66:DE:F0:2A:...
If something goes wrong like this:
Error: Could not request certificate: The certificate retrieved from the master does not match the agent's private key. ...
We can do clean-up on both sides:
master:ubuntu@ip-172-31-35-27:~$ sudo puppet cert clean agent-node.us-west-1.compute.internalclient:
ubuntu@agent-node:~$ sudo find /var/lib/puppet/ssl -name agent-node.us-west-1.compute.internal.pem -delete
Now, we have a puppet master that controls a client.
How the master tell what the clients do?
/etc/puppet/manifests/site.pp:import "nodes"
Puppet's normal behavior is to compile a single manifest (the "site manifest") and autoload any referenced classes from modules. The site.pp is the entry point for puppetmaster configuration. The file simply tells puppet to look for the nodes.pp file. Other site-wide configurations can go here as well.
/etc/puppet/manifests/nodes.pp:
node default {
}
node mytest {
include hosts
}
node 'agent-node' inherits mytest {
}
node 'agent-node-2' {
}
The first node defined here is the default node which tells puppet what to do with any client that talks to the master. However, any specific client is not mentioned in our sample nodes.pp. So, in this case, we do nothing with such clients.
The mytest node is defined to get a resource called hosts. Again, we haven't defined what nodes are in the mytest node before saying what should happen to such nodes.
The next node (agent-node) inserts actual hosts into the mytest group.The last node (agent-node-2) is a place holder for a machine that does not get anything from the mytest.
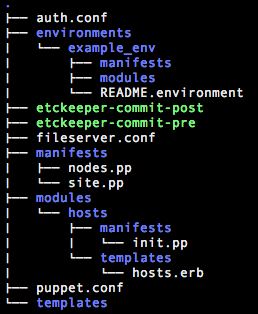
We've created a puppet module called hosts and now we the file structure as shown above.
- files: this is where puppet looks for static files that the module will push out as part of this module.
- manifests: this is where puppet gets the configuration files for this module. init.pp is the default starting point.
- templates: this is where puppet looks for templates (files that are modified before being distributed).
/etc/puppet/modules/hosts/manifests/init.pp:
class hosts {
file { "/etc/hosts":
owner => root,
group => root,
mode => 644,
content => template("hosts/hosts.erb"),
}
}
Puppet only does things that we specifically tell it to do (declarative). So, we tell it to make sure there is a file called /etc/hosts and that it specifies owner, group, permission, and content.
Below is a ruby template that contains variables and static text.
/etc/puppet/modules/hosts/templates/hosts.erb:<%= ipaddress %> <%= fqdn %> <%= hostname %> 127.0.0.1 localhost.localdomain localhost # The following lines are desirable for IPv6 capable hosts ::1 ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 ip6-allnodes ff02::2 ip6-allrouters ff02::3 ip6-allhosts 172.31.35.28 agent-node
When the template is populated, it looks like this:
127.0.0.1 localhost.localdomain localhost # The following lines are desirable for IPv6 capable hosts ::1 ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 ip6-allnodes ff02::2 ip6-allrouters ff02::3 ip6-allhosts 172.31.35.28 agent-node
Agent get puppettized when it's pulling catalog from the master. It does it every runinterval which we can check the value:
ubuntu@agent-node:~$ puppet agent --configprint runinterval 1800
In this case, it is 1800 s (30 m)
We can get the catalog immediately from the master using the "puppet agent -t":
ubuntu@agent-node:~$ sudo puppet agent -t
Info: Retrieving pluginfacts
Info: Retrieving plugin
Info: Caching catalog for agent-node.us-west-1.compute.internal
Info: Applying configuration version '1426868765'
Notice: /Stage[main]/Hosts/File[/etc/hosts]/content:
...
Info: Computing checksum on file /etc/hosts
Info: /Stage[main]/Hosts/File[/etc/hosts]: Filebucketed /etc/hosts to puppet with sum 8789c9b0fa94c79d0dffd4d9129fd25d
Notice: /Stage[main]/Hosts/File[/etc/hosts]/content: content changed '{md5}8789c9b0fa94c79d0dffd4d9129fd25d' to '{md5}81b8ae8002c5320991a68deefeb11556'
Notice: Finished catalog run in 0.23 seconds
Puppet
Ph.D. / Golden Gate Ave, San Francisco / Seoul National Univ / Carnegie Mellon / UC Berkeley / DevOps / Deep Learning / Visualization