Nagios on CentOS 7 with Nagios Remote Plugin Executor (NRPE) 2020
We've already installed Nagios 4 on Ubuntu 14.04 in our previous tutorial (Nagios - The Industry Standard in IT Infrastructure Monitoring on Ubuntu).
In this article, we'll do the same on CentOS 7 server.
After some basic configuration, we will be able to monitor host resources via the web interface.On remote hosts, Nagios Remote Plugin Executor (NRPE) will be installed as an agent to monitor their local resources.
We'll skip the steps of installing a LAMP stack.
Let's check the swap size:
$ grep SwapTotal /proc/meminfo SwapTotal: 262140 kB
2GB is OK.
We need to install a few libraries since we're building Nagios Core from source. We will also install apache2-utils to set up the Nagios web interface.
Let's install the required packages:
$ sudo yum install gcc glibc glibc-common gd gd-devel make net-snmp openssl-devel xinetd unzip apache2-utils
We may want to create a nagios user and nagcmd group, then add the nagios user to the nagcmd group:
$ sudo useradd nagios $ sudo groupadd nagcmd $ sudo usermod -a -G nagcmd nagios
Download the source code for the latest stable release of Nagios Core from .
$ cd ~ $ curl -L -O https://assets.nagios.com/downloads/nagioscore/releases/nagios-4.1.1.tar.gz
Extract the Nagios archive with this command:
$ tar xvf nagios-*.tar.gz $ cd nagios-*
We must configure it before building Nagios with this command:
$ ./configure --with-command-group=nagcmd
*** Configuration summary for nagios 4.1.1 08-19-2015 ***:
General Options:
-------------------------
Nagios executable: nagios
Nagios user/group: nagios,nagios
Command user/group: nagios,nagcmd
Event Broker: yes
Install ${prefix}: /usr/local/nagios
Install ${includedir}: /usr/local/nagios/include/nagios
Lock file: ${prefix}/var/nagios.lock
Check result directory: ${prefix}/var/spool/checkresults
Init directory: /etc/rc.d/init.d
Apache conf.d directory: /etc/httpd/conf.d
Mail program: /bin/mail
Host OS: linux-gnu
IOBroker Method: epoll
Web Interface Options:
------------------------
HTML URL: http://localhost/nagios/
CGI URL: http://localhost/nagios/cgi-bin/
Traceroute (used by WAP): /usr/bin/traceroute
Now compile Nagios:
$ make all
We can now run the following make commands to install Nagios including init scripts and sample configuration files:
$ sudo make install $ sudo make install-commandmode $ sudo make install-init $ sudo make install-config $ sudo make install-webconf
In order to issue external commands via the web interface to Nagios, we must add the web server user, apache, to the nagcmd group:
$ sudo usermod -G nagcmd apache
Download the latest release of Nagios Plugins:
$ cd ~ $ curl -L -O http://nagios-plugins.org/download/nagios-plugins-2.1.1.tar.gz $ tar xvf nagios-plugins-*.tar.gz $ cd nagios-plugins-*
We must configure Nagios Plugins before building it:
$ ./configure --with-nagios-user=nagios --with-nagios-group=nagios
Now compile Nagios Plugins with this command:
$ make
Then, install it with this command:
$ sudo make install
Install the latest stable release of Nagios Remote Plugin Executor (NRPE):
$ cd ~ $ curl -L -O http://downloads.sourceforge.net/project/nagios/nrpe-2.x/nrpe-2.15/nrpe-2.15.tar.gz $ tar xvf nrpe-*.tar.gz $ cd nrpe-* $ ./configure --enable-command-args --with-nagios-user=nagios --with-nagios-group=nagios --with-ssl=/usr/bin/openssl --with-ssl-lib=/usr/lib/x86_64-linux-gnu
Let's build and install NRPE and its xinetd startup script:
$ make all $ sudo make install $ sudo make install-xinetd $ sudo make install-daemon-config
Modify the xinetd startup script (/etc/xinetd.d/nrpe) by adding the private IP address of the our Nagios server to the end:
only_from = 127.0.0.1 45.79.90.218
Only the Nagios server will be allowed to communicate with NRPE. Restart the xinetd service to start NRPE:
$ sudo service xinetd restart
Here is the modified file:
# default: on
# description: NRPE (Nagios Remote Plugin Executor)
service nrpe
{
flags = REUSE
socket_type = stream
port = 5666
wait = no
user = nagios
group = nagios
server = /usr/local/nagios/bin/nrpe
server_args = -c /usr/local/nagios/etc/nrpe.cfg --inetd
log_on_failure += USERID
disable = no
only_from = 127.0.0.1 172.31.22.133
}
- The lines with the "#" character at the beginning are comments without any effect on the service.
- The socket_type determines the way of data transmission through the service. There are three types: stream, dgram and raw. This last one is useful, when we want to establish a service based on a non-standard protocol.
- With the user option it is possible to choose a user to be the owner of the running service. It is highly recommended to choose a non-root user for security reasons.
- The disable option is a switch to run a service or not. In most cases the default state is yes. To activate the service change it to no.
- When the wait is on yes the xinetd will not receive request for the service if it has a connection. So the number of connections is limited to one. It provides very good protection when we want to establish only one connection per time.
Now that Nagios 4 is installed, we need to configure it. Let's edit main Nagios configuration file (/usr/local/nagios/etc/nagios.cfg):
cfg_dir=/usr/local/nagios/etc/servers #cfg_dir=/usr/local/nagios/etc/printers #cfg_dir=/usr/local/nagios/etc/switches #cfg_dir=/usr/local/nagios/etc/routers
Let's create the directory that will store the configuration file for each server that we will monitor:
$ sudo mkdir /usr/local/nagios/etc/servers
Edit Nagios contacts configuration file (/usr/local/nagios/etc/objects/contacts.cfg), and replace the email value:
email sfvue@aol.com ; <<***** CHANGE THIS TO YOUR EMAIL ADDRESS ******
We need to add a new command (check_nrpe) to the end of our Nagios configuration (/usr/local/nagios/etc/objects/commands.cfg):
define command{
command_name check_nrpe
command_line $USER1$/check_nrpe -H $HOSTADDRESS$ -c $ARG1$
}
Using htpasswd we need to create an admin user, called "nagiosadmin", that can access the Nagios web interface:
$ sudo htpasswd -c /usr/local/nagios/etc/htpasswd.users nagiosadmin
Nagios is ready to be started.
Let's restart Apache:
$ sudo systemctl start nagios $ sudo systemctl restart httpd
Run the following command to enable Nagios to start on server boot:
$ sudo chkconfig nagios on
Let's go to our Nagios home page.
To access Nagios, in this tutorial, I'll use port forwarding. In other words, I'll access Nagios on port 80 from my local port 9001:
$ ssh -L 9001:localhost:80 -l sfvue 45.79.90.218
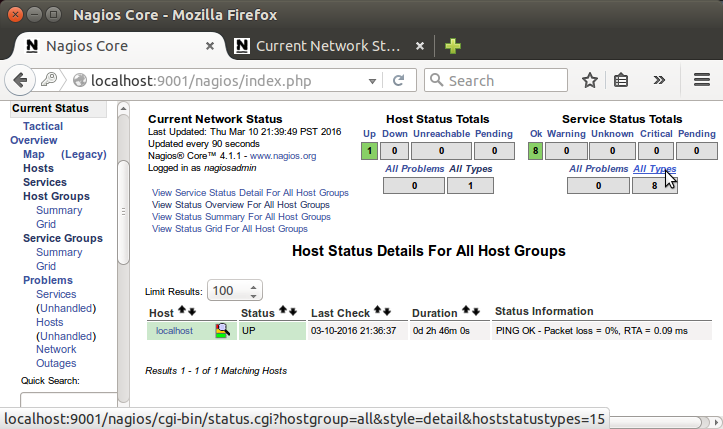
Click on the Hosts link, in the left navigation bar, to see which hosts Nagios is monitoring:
Please visit Nagios - The Industry Standard in IT Infrastructure Monitoring on Ubuntu.
Please visit Nagios - The Industry Standard in IT Infrastructure Monitoring on Ubuntu.
Please visit Nagios - The Industry Standard in IT Infrastructure Monitoring on Ubuntu.
Ph.D. / Golden Gate Ave, San Francisco / Seoul National Univ / Carnegie Mellon / UC Berkeley / DevOps / Deep Learning / Visualization