Terraform Tutorial - AWS KMS
bogotobogo.com site search:
AWS KMS
main.tf:
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "3.42.0"
}
}
}
provider "aws" {
region = var.region
}
resource "aws_kms_key" "my_kms_key" {
description = "My KMS Keys for Data Encryption"
customer_master_key_spec = var.key_spec
is_enabled = var.enabled
enable_key_rotation = var.rotation_enabled
tags = {
Name = "my_kms_key"
}
policy = <<EOF
{
"Id": "key-consolepolicy-3",
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Enable IAM User Permissions",
"Effect": "Allow",
"Principal": {
"AWS": "${var.user_arn}"
},
"Action": "kms:*",
"Resource": "*"
},
{
"Sid": "Allow access for Key Administrators",
"Effect": "Allow",
"Principal": {
"AWS": "${var.user_arn}"
},
"Action": [
"kms:Create*",
"kms:Describe*",
"kms:Enable*",
"kms:List*",
"kms:Put*",
"kms:Update*",
"kms:Revoke*",
"kms:Disable*",
"kms:Get*",
"kms:Delete*",
"kms:TagResource",
"kms:UntagResource",
"kms:ScheduleKeyDeletion",
"kms:CancelKeyDeletion"
],
"Resource": "*"
},
{
"Sid": "Allow use of the key",
"Effect": "Allow",
"Principal": {
"AWS": "${var.user_arn}"
},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*"
},
{
"Sid": "Allow attachment of persistent resources",
"Effect": "Allow",
"Principal": {
"AWS": "${var.user_arn}"
},
"Action": [
"kms:CreateGrant",
"kms:ListGrants",
"kms:RevokeGrant"
],
"Resource": "*",
"Condition": {
"Bool": {
"kms:GrantIsForAWSResource": "true"
}
}
}
]
}
EOF
}
resource "aws_kms_alias" "my_kms_alias" {
target_key_id = aws_kms_key.my_kms_key.key_id
name = "alias/${var.kms_alias}"
}
output "key_id" {
value = aws_kms_key.my_kms_key.key_id
}
variables.tf:
variable "region" {
default = "us-east-1"
}
variable "user_arn" {
default ="arn:aws:iam::047109936880:user/khong-aol"
}
variable key_spec {
default = "SYMMETRIC_DEFAULT"
}
variable enabled {
default = true
}
output "key_id" {
value = aws_kms_key.my_kms_key.key_id
}
output "key_arn" {
value = aws_kms_key.my_kms_key.arn
}
$ terraform apply --auto-approve ... aws_kms_key.my_kms_key: Creating... aws_kms_key.my_kms_key: Creation complete after 8s [id=1c86d30d-6eae-42f2-b441-d053f818b9f8] aws_kms_alias.my_kms_alias: Creating... aws_kms_alias.my_kms_alias: Creation complete after 1s [id=alias/my_encryption_key] Apply complete! Resources: 2 added, 0 changed, 0 destroyed. Outputs: key_arn = "arn:aws:kms:us-east-1:047109936880:key/1c86d30d-6eae-42f2-b441-d053f818b9f8" key_id = "1c86d30d-6eae-42f2-b441-d053f818b9f8"
We can check if the CMK has been created:
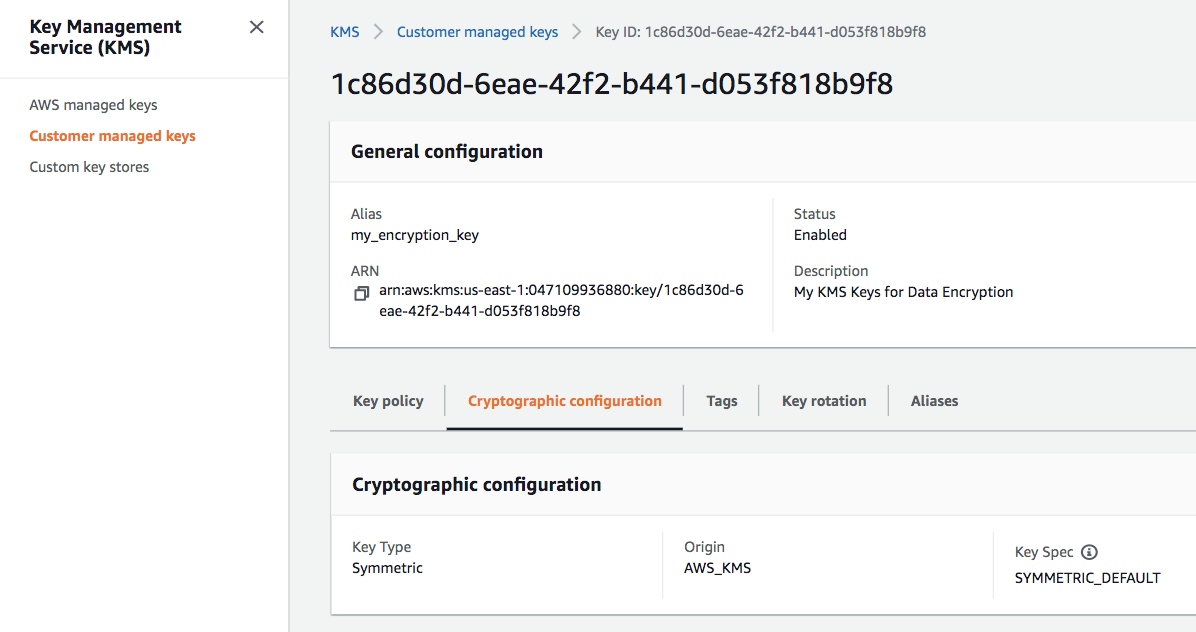
AWS KMS CLI
encrypt-text:
aws kms encrypt --key-id ${KEY_ID} --plaintext ${SECRET_TEXT} --query CiphertextBlob --output text \
| base64 --decode > "${ENCRYPTED_SECRET_AS_BLOB}"
decrypt-text:
aws kms decrypt --ciphertext-blob fileb://${ENCRYPTED_SECRET_AS_BLOB} --query Plaintext --output text \
| base64 --decode
encrypt-blob:
aws kms encrypt --key-id ${KEY_ID} --plaintext ${SECRET_BLOB_PATH} --query CiphertextBlob --output text \
| base64 --decode > ${ENCRYPTED_SECRET_AS_BLOB}
decrypt-blob:
aws kms decrypt --ciphertext-blob fileb://${ENCRYPTED_SECRET_AS_BLOB} --query Plaintext --output text \
| base64 --decode > ${DECRYPTED_SECRET_AS_BLOB}
To encrypt:
$ aws kms encrypt --key-id "1c86d30d-6eae-42f2-b441-d053f818b9f8" --plaintext "my_secret" --region us-east-1
{
"CiphertextBlob": "AQICAHj4vUsC2pjMhnfpJu7Jgqeo7XhDd6iHpSfrP214bNSCdgGEKGv5nUkr+oGfXjpBLRxxAAAAZDBiBgkqhkiG9w0BBwagVTBTAgEAME4GCSqGSIb3DQEHATAeBglghkgBZQMEAS4wEQQM27rGwugKDeGxbLWXAgEQgCGuJCcHz5w0+4IO7tHSJpF/J78SzetRfIvBxGkAYWl1uCA=",
"KeyId": "arn:aws:kms:us-east-1:047109936880:key/1c86d30d-6eae-42f2-b441-d053f818b9f8",
"EncryptionAlgorithm": "SYMMETRIC_DEFAULT"
}
$ aws kms encrypt --key-id "1c86d30d-6eae-42f2-b441-d053f818b9f8" --plaintext "my_secret" --region us-east-1 | jq -r '.CiphertextBlob'
AQICAHj4vUsC2pjMhnfpJu7Jgqeo7XhDd6iHpSfrP214bNSCdgGF0DVxjGgKkOnu1U0o23riAAAAZDBiBgkqhkiG9w0BBwagVTBTAgEAME4GCSqGSIb3DQEHATAeBglghkgBZQMEAS4wEQQM6bO1ohJrwCtm0FT3AgEQgCGaHsZh8Ggfdy2ZVH/gfLkEJqMEzPOXmq0Dum4n2qw+U9s=
$ ENCRYPTED_SECRET=$(aws kms encrypt --key-id "1c86d30d-6eae-42f2-b441-d053f818b9f8" --plaintext "my_secret" --region us-east-1 | jq -r '.CiphertextBlob')
$ echo $ENCRYPTED_SECRET
AQICAHj4vUsC2pjMhnfpJu7Jgqeo7XhDd6iHpSfrP214bNSCdgFTmnGnIyiqTFYsbcP8vMPKAAAAZDBiBgkqhkiG9w0BBwagVTBTAgEAME4GCSqGSIb3DQEHATAeBglghkgBZQMEAS4wEQQMEhsvXwML6yLfWwdIAgEQgCHpk5mAU/UhkiDcpxx4+WHJISuDhkJ389Ta5iNefE63ydo=
To decrypt:
$ $ aws kms decrypt --key-id "1c86d30d-6eae-42f2-b441-d053f818b9f8" --ciphertext-blob ${ENCRYPTED_SECRET} --region us-east-1
{
"KeyId": "arn:aws:kms:us-east-1:047109936880:key/1c86d30d-6eae-42f2-b441-d053f818b9f8",
"Plaintext": "mysecret",
"EncryptionAlgorithm": "SYMMETRIC_DEFAULT"
}
$ aws kms decrypt --key-id alias/my_encryption_key --ciphertext-blob ${ENCRYPTED_SECRET} --region us-east-1
{
"KeyId": "arn:aws:kms:us-east-1:047109936880:key/1c86d30d-6eae-42f2-b441-d053f818b9f8",
"Plaintext": "mysecret",
"EncryptionAlgorithm": "SYMMETRIC_DEFAULT"
}
Note that we can use either key-id or alias/my_encryption_key for Key ID. Also, in the command, we need to convert an env variable into binary data with echo $variable | base64 --decode because the --ciphertext-blob option expects binary data.
Terraform
Ph.D. / Golden Gate Ave, San Francisco / Seoul National Univ / Carnegie Mellon / UC Berkeley / DevOps / Deep Learning / Visualization