Docker Compose - Hashicorp's Vault and Consul Part B (EaaS, dynamic secrets, leases, and revocation)
Continued from Docker Compose - Hashicorp's Vault and Consul Part A (install vault, unsealing, static secrets, and policies), in this post, we'll see additional features of Vault such as EaaS (Encryption as a Service), dynamic secrets, leases, and revocation.
At the end of this post, we'll have the following directories/files:
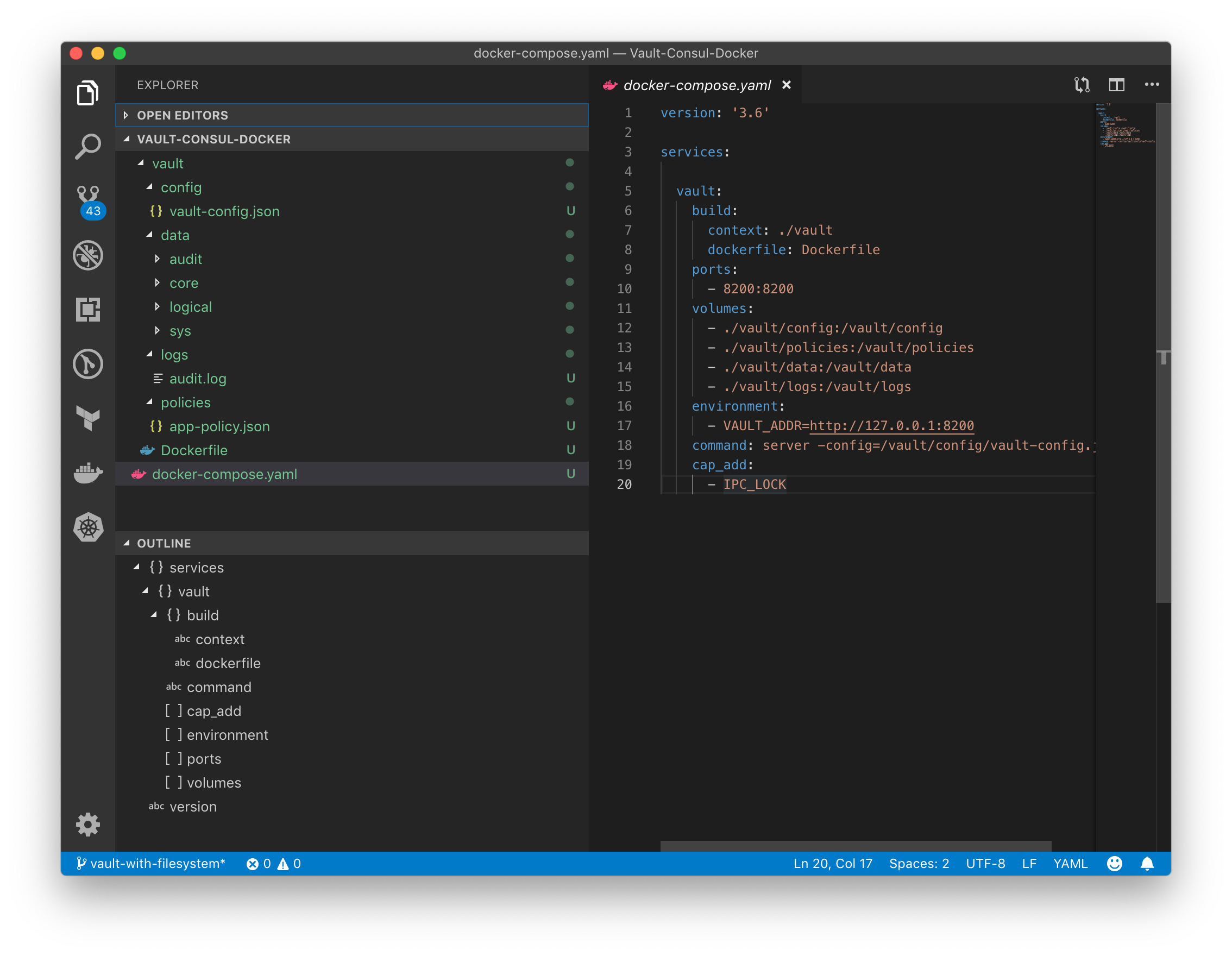
More files will show up if we expand the directories. Most of them were created by Vault.
Before we look at dynamic secrets, we may want to review the Transit backend, which can be used as an "encryption as a service" for:
- Encrypting and decrypting data "in-transit" without storing it inside Vault.
- Easily integrating encryption into our application workflow.
The primary use case for transit is to encrypt data from applications while still storing that encrypted data in some primary data store. This relieves the burden of proper encryption/decryption from application developers and pushes the burden onto the operators of Vault.
Let's go back to the bash session in the container, enable the Transit secrets engine:
bash-4.4# vault secrets enable transit Success! Enabled the transit secrets engine at: transit/
Then, configure a named encryption key:
bash-4.4# vault write -f transit/keys/foo Success! Data written to: transit/keys/foo
Usually each application has its own encryption key.
Encrypt:
bash-4.4# vault write transit/encrypt/foo plaintext=$(base64 <<< "my precious") Key Value --- ----- ciphertext vault:v1:7FEiJbqZwbo7cCBopwO2OFbXeCYG/0WlinU77oihPiDfhkN+t0v55Q==
Decrypt:
bash-4.4# vault write transit/decrypt/foo ciphertext=vault:v1:7FEiJbqZwbo7cCBopwO2OFbXeCYG/0WlinU77oihPiDfhkN+t0v55Q== Key Value --- ----- plaintext bXkgcHJlY2lvdXMK
Decode:
bash-4.4# base64 -d <<< "bXkgcHJlY2lvdXMK" my precious
Now we can test with UI:
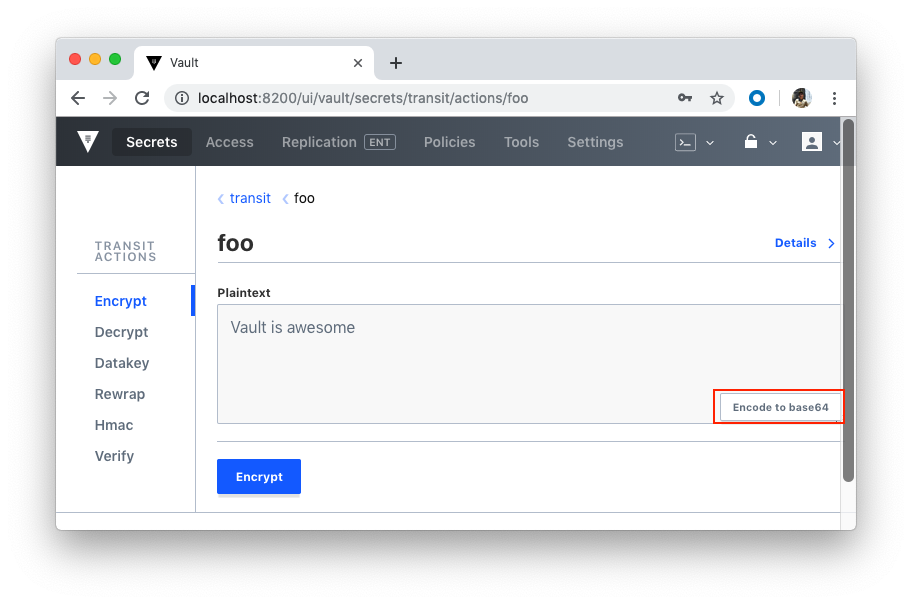
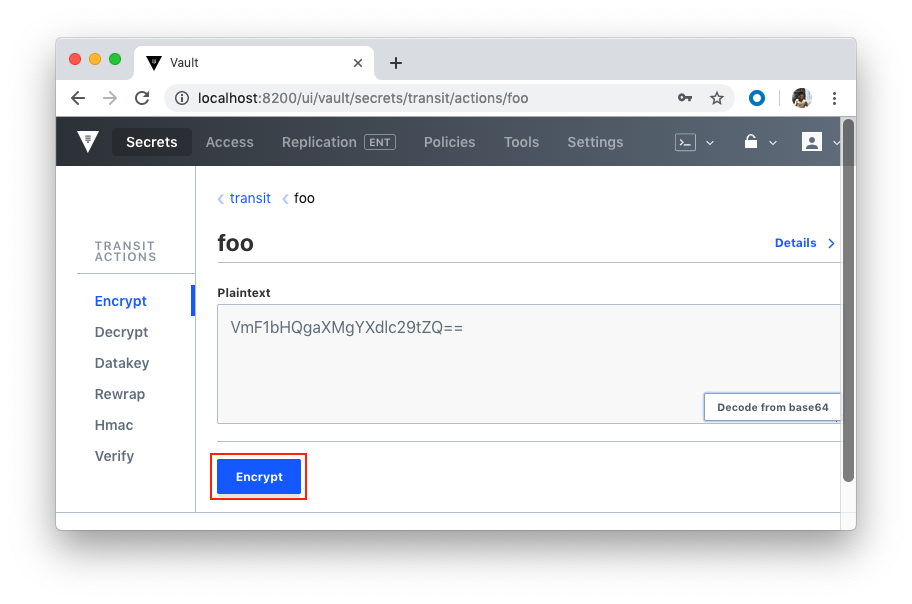
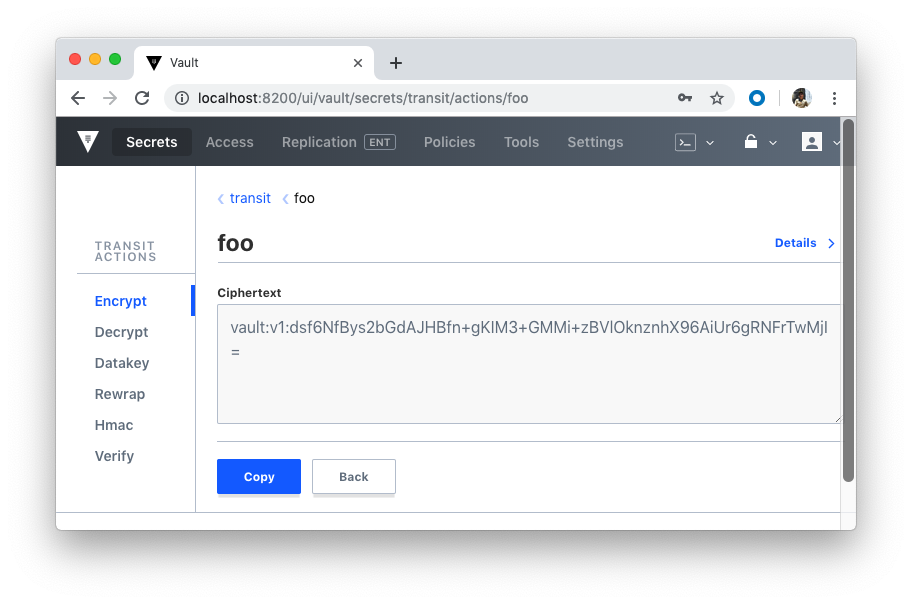
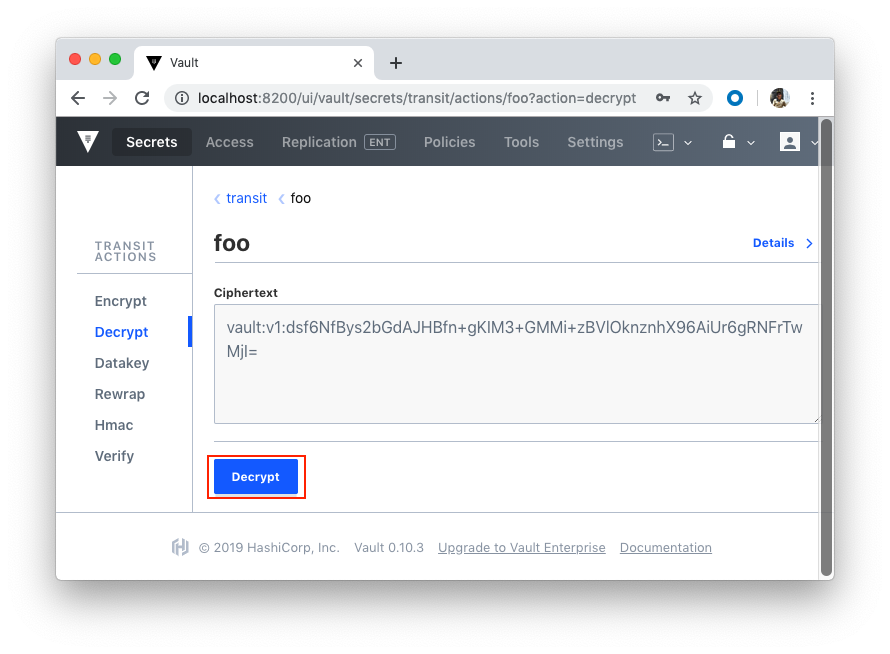
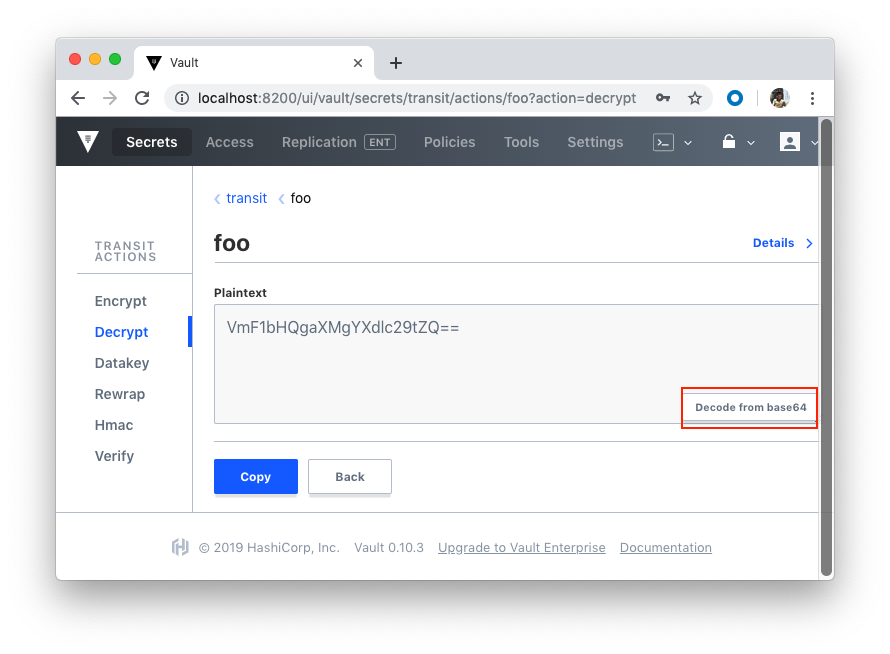
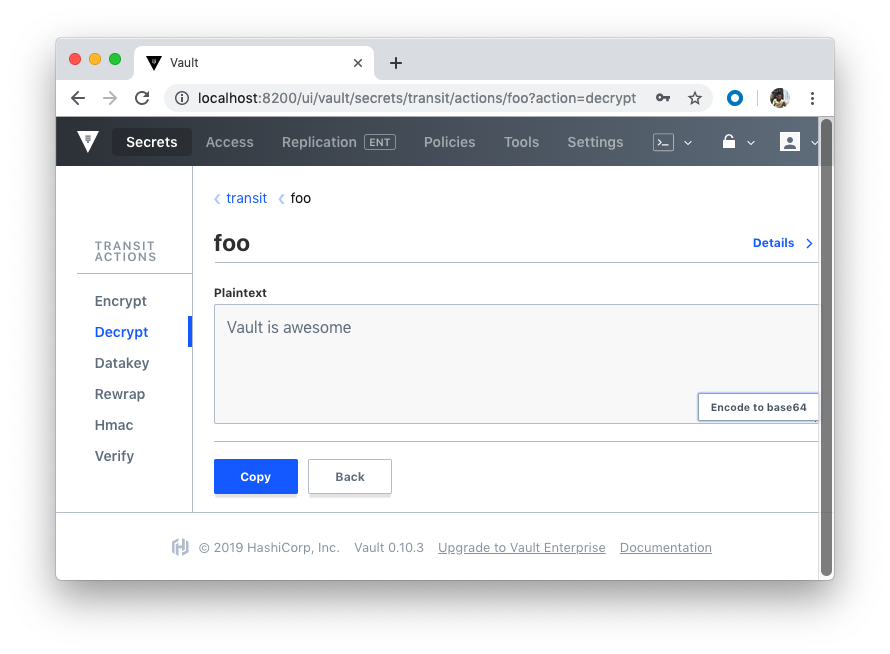
As we already know, Vault supports a number of dynamic secret backends for generating secrets dynamically when needed. For example, with the AWS and Google Cloud backends, we can create access credentials based on IAM policies. The Databases backend, meanwhile, generates database credentials based on configured roles.
Dynamic Secrets are generated on demand. They have limited access based on role, and they are leased for a period of time. They can be revoked and come with an audit trail.
As an example, let's look at how to generate AWS credentials using the AWS backend. Let's enable the AWS secrets backend:
bash-4.4# vault secrets enable -path=aws aws Success! Enabled the aws secrets engine at: aws/
Authenticate with our own AWS credentials:
# vault write aws/config/root access_key=A...A secret_key=P...7 Success! Data written to: aws/config/root
Then, create a role:
bash-4.4# vault write aws/roles/ec2-read arn=arn:aws:iam::aws:policy/AmazonEC2ReadOnlyAccess Success! Data written to: aws/roles/ec2-read
Here, we created a new role based on AmazonEC2ReadOnlyAccess, which is an AWS-managed policy. As the name suggests, it give users read-only access to the EC2 console; they cannot perform any actions or create new resources. We can also use an inline policy to create a custom role based on our individual needs.
Create a new set of credentials:
bash-4.4# vault read aws/creds/ec2-read Key Value --- ----- lease_id aws/creds/ec2-read/8c26c68b-627b-36f4-8319-d6aaaf8f3b26 lease_duration 768h lease_renewable true access_key AKIAQV57YS3YIBOZLJUS secret_key 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 security_token <nil>
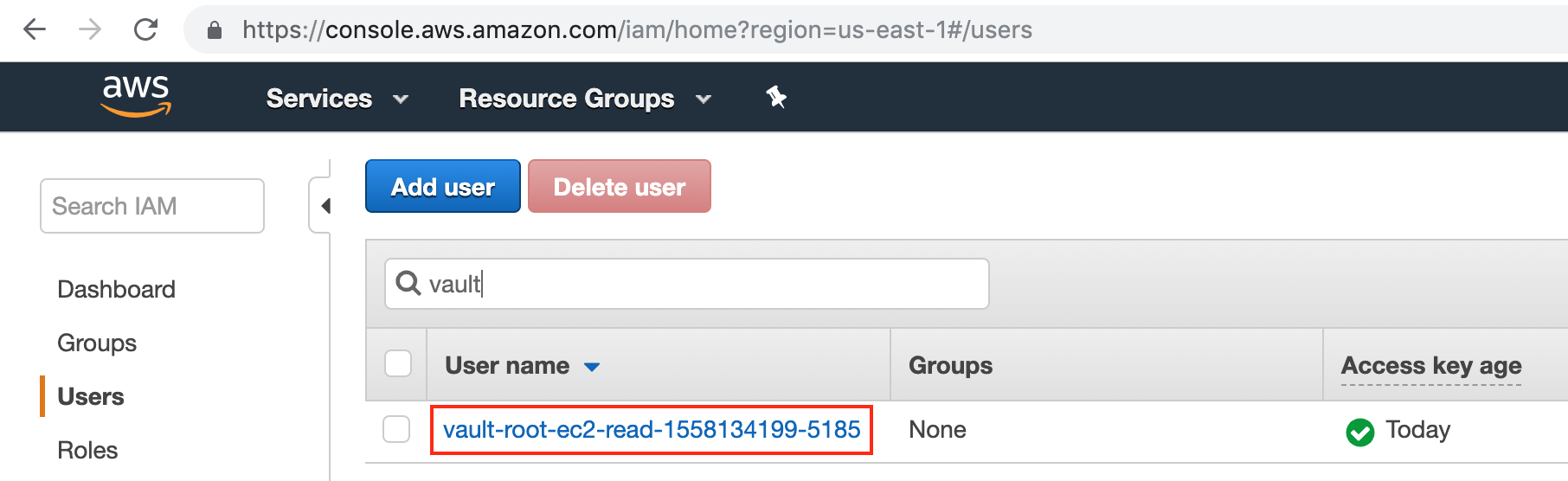
We should now be able to see the user within the "Users" section on the IAM console on AWS:
In this section we'll learn how to define a custom lease period and revoke a secret before the end of that period.
Let's create a new AWS role:
bash-4.4# vault write aws/roles/foo \ > policy=-<{ > "Version": "2012-10-17", > "Statement": [ { "Effect": "Allow", "Action": "ec2:*", "Resource": "*" } ] > } > EOF Success! Data written to: aws/roles/foo bash-4.4# vault read aws/creds/foo Key Value --- ----- lease_id aws/creds/foo/f14d1c46-6b7e-0658-bdab-4adc3cf67083 lease_duration 768h lease_renewable true access_key AKIAQV57YS3YEWJ6FBXE secret_key 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 security_token <nil>
Note that we have the lease_duration!
If we want the lease period for all AWS IAM dynamic secrets to be 30 minutes:
bash-4.4# vault write aws/config/lease lease=1800s lease_max=3600s Success! Data written to: aws/config/lease
Since we set the lease_max to 3600s, we'll be able to renew the lease once.
For a revoking example, let's create a new credential:
bash-4.4# vault read aws/creds/foo Key Value --- ----- lease_id aws/creds/foo/5b586c22-4192-5111-af7d-804a4aacfa2b lease_duration 30m lease_renewable true access_key AKIAQV57YS3YINO5YUC3 secret_key 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 security_token <nil>
To revoke this credential, we may want to grab the lease_id and then run the following:
bash-4.4# vault lease revoke aws/creds/foo/5b586c22-4192-5111-af7d-804a4aacfa2b Success! Revoked lease: aws/creds/foo/5b586c22-4192-5111-af7d-804a4aacfa2b
To revoke all AWS creds:
bash-4.4# vault revoke -prefix aws/ WARNING! The "vault revoke" command is deprecated. Please use "vault lease revoke" instead. This command will be removed in Vault 0.11 (or later). Success! Revoked any leases with prefix: aws/
- Managing Secrets with Vault and Consul
- HashiCorp Docs
- Docker & Kubernetes : HashiCorp's Vault and Consul on minikube
- Docker & Kubernetes : HashiCorp's Vault and Consul - Auto-unseal using Transit Secrets Engine
- HashiCorp Vault and Consul on AWS with Terraform
- Code Repo: Docker-compose-Hashicorp-Vault-Consul
Continued to Docker Compose - Hashicorp's Vault and Consul Part C (Consul).
Docker & K8s
- Docker install on Amazon Linux AMI
- Docker install on EC2 Ubuntu 14.04
- Docker container vs Virtual Machine
- Docker install on Ubuntu 14.04
- Docker Hello World Application
- Nginx image - share/copy files, Dockerfile
- Working with Docker images : brief introduction
- Docker image and container via docker commands (search, pull, run, ps, restart, attach, and rm)
- More on docker run command (docker run -it, docker run --rm, etc.)
- Docker Networks - Bridge Driver Network
- Docker Persistent Storage
- File sharing between host and container (docker run -d -p -v)
- Linking containers and volume for datastore
- Dockerfile - Build Docker images automatically I - FROM, MAINTAINER, and build context
- Dockerfile - Build Docker images automatically II - revisiting FROM, MAINTAINER, build context, and caching
- Dockerfile - Build Docker images automatically III - RUN
- Dockerfile - Build Docker images automatically IV - CMD
- Dockerfile - Build Docker images automatically V - WORKDIR, ENV, ADD, and ENTRYPOINT
- Docker - Apache Tomcat
- Docker - NodeJS
- Docker - NodeJS with hostname
- Docker Compose - NodeJS with MongoDB
- Docker - Prometheus and Grafana with Docker-compose
- Docker - StatsD/Graphite/Grafana
- Docker - Deploying a Java EE JBoss/WildFly Application on AWS Elastic Beanstalk Using Docker Containers
- Docker : NodeJS with GCP Kubernetes Engine
- Docker : Jenkins Multibranch Pipeline with Jenkinsfile and Github
- Docker : Jenkins Master and Slave
- Docker - ELK : ElasticSearch, Logstash, and Kibana
- Docker - ELK 7.6 : Elasticsearch on Centos 7
- Docker - ELK 7.6 : Filebeat on Centos 7
- Docker - ELK 7.6 : Logstash on Centos 7
- Docker - ELK 7.6 : Kibana on Centos 7
- Docker - ELK 7.6 : Elastic Stack with Docker Compose
- Docker - Deploy Elastic Cloud on Kubernetes (ECK) via Elasticsearch operator on minikube
- Docker - Deploy Elastic Stack via Helm on minikube
- Docker Compose - A gentle introduction with WordPress
- Docker Compose - MySQL
- MEAN Stack app on Docker containers : micro services
- MEAN Stack app on Docker containers : micro services via docker-compose
- Docker Compose - Hashicorp's Vault and Consul Part A (install vault, unsealing, static secrets, and policies)
- Docker Compose - Hashicorp's Vault and Consul Part B (EaaS, dynamic secrets, leases, and revocation)
- Docker Compose - Hashicorp's Vault and Consul Part C (Consul)
- Docker Compose with two containers - Flask REST API service container and an Apache server container
- Docker compose : Nginx reverse proxy with multiple containers
- Docker & Kubernetes : Envoy - Getting started
- Docker & Kubernetes : Envoy - Front Proxy
- Docker & Kubernetes : Ambassador - Envoy API Gateway on Kubernetes
- Docker Packer
- Docker Cheat Sheet
- Docker Q & A #1
- Kubernetes Q & A - Part I
- Kubernetes Q & A - Part II
- Docker - Run a React app in a docker
- Docker - Run a React app in a docker II (snapshot app with nginx)
- Docker - NodeJS and MySQL app with React in a docker
- Docker - Step by Step NodeJS and MySQL app with React - I
- Installing LAMP via puppet on Docker
- Docker install via Puppet
- Nginx Docker install via Ansible
- Apache Hadoop CDH 5.8 Install with QuickStarts Docker
- Docker - Deploying Flask app to ECS
- Docker Compose - Deploying WordPress to AWS
- Docker - WordPress Deploy to ECS with Docker-Compose (ECS-CLI EC2 type)
- Docker - WordPress Deploy to ECS with Docker-Compose (ECS-CLI Fargate type)
- Docker - ECS Fargate
- Docker - AWS ECS service discovery with Flask and Redis
- Docker & Kubernetes : minikube
- Docker & Kubernetes 2 : minikube Django with Postgres - persistent volume
- Docker & Kubernetes 3 : minikube Django with Redis and Celery
- Docker & Kubernetes 4 : Django with RDS via AWS Kops
- Docker & Kubernetes : Kops on AWS
- Docker & Kubernetes : Ingress controller on AWS with Kops
- Docker & Kubernetes : HashiCorp's Vault and Consul on minikube
- Docker & Kubernetes : HashiCorp's Vault and Consul - Auto-unseal using Transit Secrets Engine
- Docker & Kubernetes : Persistent Volumes & Persistent Volumes Claims - hostPath and annotations
- Docker & Kubernetes : Persistent Volumes - Dynamic volume provisioning
- Docker & Kubernetes : DaemonSet
- Docker & Kubernetes : Secrets
- Docker & Kubernetes : kubectl command
- Docker & Kubernetes : Assign a Kubernetes Pod to a particular node in a Kubernetes cluster
- Docker & Kubernetes : Configure a Pod to Use a ConfigMap
- AWS : EKS (Elastic Container Service for Kubernetes)
- Docker & Kubernetes : Run a React app in a minikube
- Docker & Kubernetes : Minikube install on AWS EC2
- Docker & Kubernetes : Cassandra with a StatefulSet
- Docker & Kubernetes : Terraform and AWS EKS
- Docker & Kubernetes : Pods and Service definitions
- Docker & Kubernetes : Service IP and the Service Type
- Docker & Kubernetes : Kubernetes DNS with Pods and Services
- Docker & Kubernetes : Headless service and discovering pods
- Docker & Kubernetes : Scaling and Updating application
- Docker & Kubernetes : Horizontal pod autoscaler on minikubes
- Docker & Kubernetes : From a monolithic app to micro services on GCP Kubernetes
- Docker & Kubernetes : Rolling updates
- Docker & Kubernetes : Deployments to GKE (Rolling update, Canary and Blue-green deployments)
- Docker & Kubernetes : Slack Chat Bot with NodeJS on GCP Kubernetes
- Docker & Kubernetes : Continuous Delivery with Jenkins Multibranch Pipeline for Dev, Canary, and Production Environments on GCP Kubernetes
- Docker & Kubernetes : NodePort vs LoadBalancer vs Ingress
- Docker & Kubernetes : MongoDB / MongoExpress on Minikube
- Docker & Kubernetes : Load Testing with Locust on GCP Kubernetes
- Docker & Kubernetes : MongoDB with StatefulSets on GCP Kubernetes Engine
- Docker & Kubernetes : Nginx Ingress Controller on Minikube
- Docker & Kubernetes : Setting up Ingress with NGINX Controller on Minikube (Mac)
- Docker & Kubernetes : Nginx Ingress Controller for Dashboard service on Minikube
- Docker & Kubernetes : Nginx Ingress Controller on GCP Kubernetes
- Docker & Kubernetes : Kubernetes Ingress with AWS ALB Ingress Controller in EKS
- Docker & Kubernetes : Setting up a private cluster on GCP Kubernetes
- Docker & Kubernetes : Kubernetes Namespaces (default, kube-public, kube-system) and switching namespaces (kubens)
- Docker & Kubernetes : StatefulSets on minikube
- Docker & Kubernetes : RBAC
- Docker & Kubernetes Service Account, RBAC, and IAM
- Docker & Kubernetes - Kubernetes Service Account, RBAC, IAM with EKS ALB, Part 1
- Docker & Kubernetes : Helm Chart
- Docker & Kubernetes : My first Helm deploy
- Docker & Kubernetes : Readiness and Liveness Probes
- Docker & Kubernetes : Helm chart repository with Github pages
- Docker & Kubernetes : Deploying WordPress and MariaDB with Ingress to Minikube using Helm Chart
- Docker & Kubernetes : Deploying WordPress and MariaDB to AWS using Helm 2 Chart
- Docker & Kubernetes : Deploying WordPress and MariaDB to AWS using Helm 3 Chart
- Docker & Kubernetes : Helm Chart for Node/Express and MySQL with Ingress
- Docker & Kubernetes : Deploy Prometheus and Grafana using Helm and Prometheus Operator - Monitoring Kubernetes node resources out of the box
- Docker & Kubernetes : Deploy Prometheus and Grafana using kube-prometheus-stack Helm Chart
- Docker & Kubernetes : Istio (service mesh) sidecar proxy on GCP Kubernetes
- Docker & Kubernetes : Istio on EKS
- Docker & Kubernetes : Istio on Minikube with AWS EC2 for Bookinfo Application
- Docker & Kubernetes : Deploying .NET Core app to Kubernetes Engine and configuring its traffic managed by Istio (Part I)
- Docker & Kubernetes : Deploying .NET Core app to Kubernetes Engine and configuring its traffic managed by Istio (Part II - Prometheus, Grafana, pin a service, split traffic, and inject faults)
- Docker & Kubernetes : Helm Package Manager with MySQL on GCP Kubernetes Engine
- Docker & Kubernetes : Deploying Memcached on Kubernetes Engine
- Docker & Kubernetes : EKS Control Plane (API server) Metrics with Prometheus
- Docker & Kubernetes : Spinnaker on EKS with Halyard
- Docker & Kubernetes : Continuous Delivery Pipelines with Spinnaker and Kubernetes Engine
- Docker & Kubernetes : Multi-node Local Kubernetes cluster : Kubeadm-dind (docker-in-docker)
- Docker & Kubernetes : Multi-node Local Kubernetes cluster : Kubeadm-kind (k8s-in-docker)
- Docker & Kubernetes : nodeSelector, nodeAffinity, taints/tolerations, pod affinity and anti-affinity - Assigning Pods to Nodes
- Docker & Kubernetes : Jenkins-X on EKS
- Docker & Kubernetes : ArgoCD App of Apps with Heml on Kubernetes
- Docker & Kubernetes : ArgoCD on Kubernetes cluster
- Docker & Kubernetes : GitOps with ArgoCD for Continuous Delivery to Kubernetes clusters (minikube) - guestbook
Ph.D. / Golden Gate Ave, San Francisco / Seoul National Univ / Carnegie Mellon / UC Berkeley / DevOps / Deep Learning / Visualization