AWS : VPC (Virtual Private Cloud) 1 - netmask, subnets, default gateway, and CIDR
Configuring complex environments for VPC requires deep understanding of networking. VPC is about communicating between servers efficiently, developing secure network policies, and keeping our nodes organized.
In this chapter, we will discuss the concepts that are involved with designing or interacting with networked computers such as subnets and CIDR notation for grouping IP addresses.
While IPv6 is becoming more common, in this article, we will be studying the remaining concepts using IPv4 addresses because it is much easier to discuss since its smaller address space.
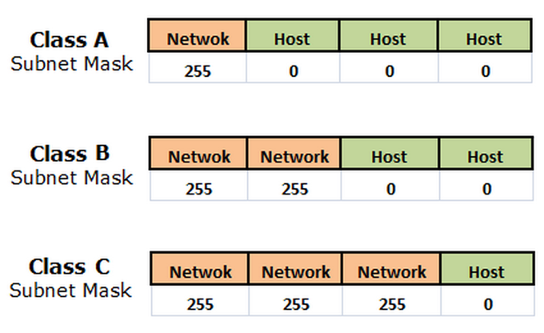
IP addresses are made of two separate components. The first part of the address is used to identify the network, and the other past is used to specify a specific host within that network.
There are also some portions of the IPv4 space that are reserved for specific uses.
One of the most useful reserved ranges is the loopback range specified by addresses from 127.0.0.0 to 127.255.255.255. This range is used by each host to test networking to itself. Typically, this is expressed by the first address in this range: 127.0.0.1.
Each of the normal classes also have a range within them that is used to designate private network addresses.
- class A
10.0.0.0 - 10.255.255.255 - class B
172.16.0.0 - 172.31.255.255 - class C
192.168.0.0 - 192.168.255.255
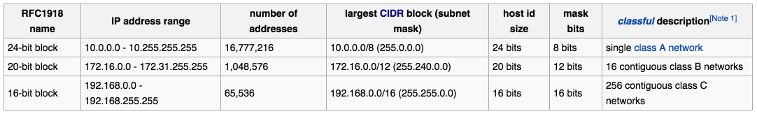
Picture from Private network - wiki
Subnetting is the process of dividing a network into smaller network sections. This helps to isolate groups of hosts together.
As we discussed in the section (IP addresses), each address space is divided into a network portion and a host portion. For instance, for class C addresses, the first 3 octets are used to describe the network. For the address 192.168.0.12, the 192.168.0 portion describes the network and the 12 describes the host.
Each network, by default, has only one subnet, which contains all of the host addresses defined within. A netmask is basically a specification of the amount of address bits that are used for the network portion. A subnet mask is another netmask within used to further divide the network.
Each bit of the address that is considered significant for describing the network should be represented as a "1" in the netmask.
For instance, the address we discussed above, in a binary format, 192.168.0.12 looks like this:
1100 0000 - 1010 1000 - 0000 0000 - 0000 1100
The network portion for class C addresses is the first 3 octets, or the first 24 bits. Since these are the significant bits that we want to preserve, the netmask would be:
1111 1111 - 1111 1111 - 1111 1111 - 0000 0000
In the normal IPv4 format, this can be expressed as 255.255.255.0. Any bit that is a "0" in the binary representation of the netmask is considered part of the host portion of the address.
We determine the network portion of the address by applying a bitwise AND operation to between the address and the netmask. A bitwise AND operation will basically save the networking portion of the address and discard the host portion. The result of this on our above example that represents our network is:
1100 0000 - 1010 1000 - 0000 0000 - 0000 1100 address 1111 1111 - 1111 1111 - 1111 1111 - 0000 0000 netmast ---------------------------------------------- 1100 0000 - 1010 1000 - 0000 0000 - 0000 0000 network
This can be expressed as 192.168.0.0. The host specification is then the difference between these original value and the host portion. In our case, the host is "0000 1100" or 12.
Subnetting is to take a portion of the host space of an address, and use it as an additional networking specification to divide the address space again.
For instance, a netmask of 255.255.255.0 as we saw in previous section leaves us with 254 hosts in the network (Note that we cannot end in 0 or 255 because these are reserved). If we wanted to divide this into two subnetworks, we could use one bit of the conventional host portion of the address as the subnet mask.
For the sample (192.168.0.12), the networking portion is:
1100 0000 - 1010 1000 - 0000 0000
Host portion is:
0000 1100
We can use the first bit of our host to designate a sub-network. We can do this by adjusting the subnet mask from:
1111 1111 - 1111 1111 - 1111 1111 - 0000 0000
To :
1111 1111 - 1111 1111 - 1111 1111 - 1000 0000
This netmask can be expressed as 192.168.0.128.
We designated the first bit of the last octet as significant in addressing the network! This effectively produced two subnetworks.
- The first subnetwork is from 192.168.0.1 to 192.168.0.127.
- The second subnetwork contains the hosts 192.168.0.129 to 192.168.0.255.
Note that the subnet itself must not be used as an address.
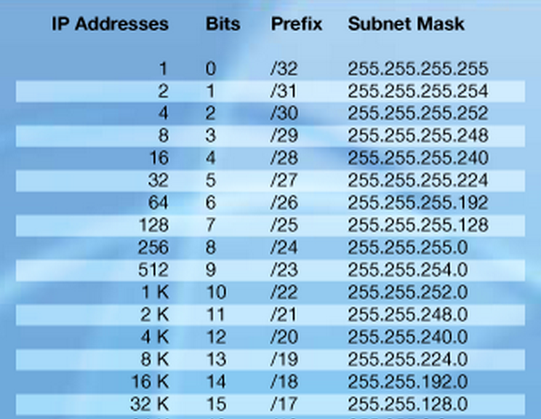
Classless Inter-Domain Routing (CIDR) is a method for allocating IP addresses and routing Internet Protocol packets.
It is an IP addressing scheme that replaces the older system based on classes A, B, and C.
A single IP address can be used to designate many unique IP addresses with CIDR. A CIDR IP address looks like a normal IP address except that it ends with a slash followed by a number, called the IP network prefix.
CIDR addresses reduce the size of routing tables and make more IP addresses available within organizations.
To be more specific, let's use the example in the previous sections.
We can express the idea that the IP address 192.168.0.12 is associated with the netmask 255.255.255.0 by using the CIDR notation of 192.168.0.12/24. This means that the first 24 bits of the IP address given are considered significant for the network routing.
A default gateway in computer networking, is the node that is assumed to know how to forward packets on to other networks.
Typically, in a TCP/IP network, nodes such as servers, workstations and network devices each have a defined default route setting, (pointing to the default gateway), defining where to send packets for IP addresses for which they can determine specific route. The gateway is by definition a router.
As a simple example, let's think about the following 2 networks :
-
Network: 192.168.1.0/30 Gateway: 192.168.1.1 Usable: 192.168.1.2 Broadcast: 192.168.1.3
-
Network: 192.168.1.0/29 Gateway: 192.168.1.1 Usable: 192.168.1.2-6 Broadcast: 192.168.1.7
Note that /29 may cover a range of 8 addresses, but only 5 of them can be used as host endpoints. /30 has only 1 usable address.
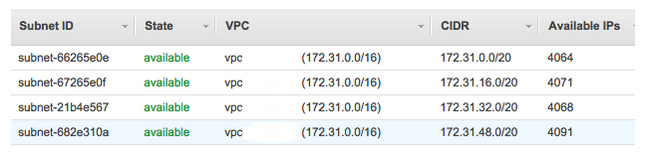
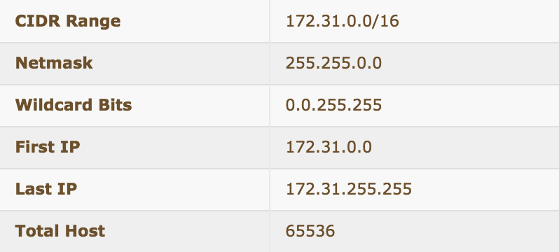
- 172.31.0.0/20
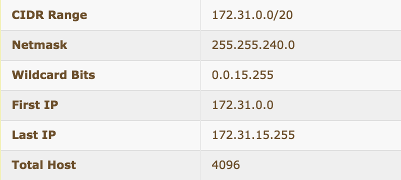
- 172.31.16.0/20
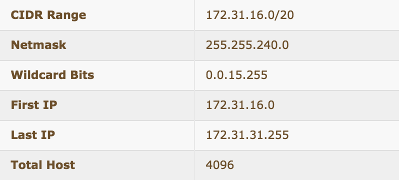
- 172.31.32.0/20
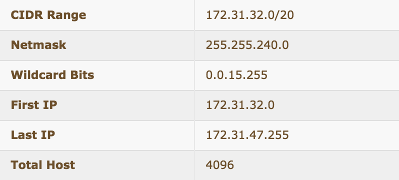
- 172.31.48.0/20
AWS (Amazon Web Services)
- AWS : EKS (Elastic Container Service for Kubernetes)
- AWS : Creating a snapshot (cloning an image)
- AWS : Attaching Amazon EBS volume to an instance
- AWS : Adding swap space to an attached volume via mkswap and swapon
- AWS : Creating an EC2 instance and attaching Amazon EBS volume to the instance using Python boto module with User data
- AWS : Creating an instance to a new region by copying an AMI
- AWS : S3 (Simple Storage Service) 1
- AWS : S3 (Simple Storage Service) 2 - Creating and Deleting a Bucket
- AWS : S3 (Simple Storage Service) 3 - Bucket Versioning
- AWS : S3 (Simple Storage Service) 4 - Uploading a large file
- AWS : S3 (Simple Storage Service) 5 - Uploading folders/files recursively
- AWS : S3 (Simple Storage Service) 6 - Bucket Policy for File/Folder View/Download
- AWS : S3 (Simple Storage Service) 7 - How to Copy or Move Objects from one region to another
- AWS : S3 (Simple Storage Service) 8 - Archiving S3 Data to Glacier
- AWS : Creating a CloudFront distribution with an Amazon S3 origin
- AWS : Creating VPC with CloudFormation
- AWS : WAF (Web Application Firewall) with preconfigured CloudFormation template and Web ACL for CloudFront distribution
- AWS : CloudWatch & Logs with Lambda Function / S3
- AWS : Lambda Serverless Computing with EC2, CloudWatch Alarm, SNS
- AWS : Lambda and SNS - cross account
- AWS : CLI (Command Line Interface)
- AWS : CLI (ECS with ALB & autoscaling)
- AWS : ECS with cloudformation and json task definition
- AWS Application Load Balancer (ALB) and ECS with Flask app
- AWS : Load Balancing with HAProxy (High Availability Proxy)
- AWS : VirtualBox on EC2
- AWS : NTP setup on EC2
- AWS: jq with AWS
- AWS & OpenSSL : Creating / Installing a Server SSL Certificate
- AWS : OpenVPN Access Server 2 Install
- AWS : VPC (Virtual Private Cloud) 1 - netmask, subnets, default gateway, and CIDR
- AWS : VPC (Virtual Private Cloud) 2 - VPC Wizard
- AWS : VPC (Virtual Private Cloud) 3 - VPC Wizard with NAT
- DevOps / Sys Admin Q & A (VI) - AWS VPC setup (public/private subnets with NAT)
- AWS - OpenVPN Protocols : PPTP, L2TP/IPsec, and OpenVPN
- AWS : Autoscaling group (ASG)
- AWS : Setting up Autoscaling Alarms and Notifications via CLI and Cloudformation
- AWS : Adding a SSH User Account on Linux Instance
- AWS : Windows Servers - Remote Desktop Connections using RDP
- AWS : Scheduled stopping and starting an instance - python & cron
- AWS : Detecting stopped instance and sending an alert email using Mandrill smtp
- AWS : Elastic Beanstalk with NodeJS
- AWS : Elastic Beanstalk Inplace/Rolling Blue/Green Deploy
- AWS : Identity and Access Management (IAM) Roles for Amazon EC2
- AWS : Identity and Access Management (IAM) Policies, sts AssumeRole, and delegate access across AWS accounts
- AWS : Identity and Access Management (IAM) sts assume role via aws cli2
- AWS : Creating IAM Roles and associating them with EC2 Instances in CloudFormation
- AWS Identity and Access Management (IAM) Roles, SSO(Single Sign On), SAML(Security Assertion Markup Language), IdP(identity provider), STS(Security Token Service), and ADFS(Active Directory Federation Services)
- AWS : Amazon Route 53
- AWS : Amazon Route 53 - DNS (Domain Name Server) setup
- AWS : Amazon Route 53 - subdomain setup and virtual host on Nginx
- AWS Amazon Route 53 : Private Hosted Zone
- AWS : SNS (Simple Notification Service) example with ELB and CloudWatch
- AWS : Lambda with AWS CloudTrail
- AWS : SQS (Simple Queue Service) with NodeJS and AWS SDK
- AWS : Redshift data warehouse
- AWS : CloudFormation
- AWS : CloudFormation Bootstrap UserData/Metadata
- AWS : CloudFormation - Creating an ASG with rolling update
- AWS : Cloudformation Cross-stack reference
- AWS : OpsWorks
- AWS : Network Load Balancer (NLB) with Autoscaling group (ASG)
- AWS CodeDeploy : Deploy an Application from GitHub
- AWS EC2 Container Service (ECS)
- AWS EC2 Container Service (ECS) II
- AWS Hello World Lambda Function
- AWS Lambda Function Q & A
- AWS Node.js Lambda Function & API Gateway
- AWS API Gateway endpoint invoking Lambda function
- AWS API Gateway invoking Lambda function with Terraform
- AWS API Gateway invoking Lambda function with Terraform - Lambda Container
- Amazon Kinesis Streams
- AWS: Kinesis Data Firehose with Lambda and ElasticSearch
- Amazon DynamoDB
- Amazon DynamoDB with Lambda and CloudWatch
- Loading DynamoDB stream to AWS Elasticsearch service with Lambda
- Amazon ML (Machine Learning)
- Simple Systems Manager (SSM)
- AWS : RDS Connecting to a DB Instance Running the SQL Server Database Engine
- AWS : RDS Importing and Exporting SQL Server Data
- AWS : RDS PostgreSQL & pgAdmin III
- AWS : RDS PostgreSQL 2 - Creating/Deleting a Table
- AWS : MySQL Replication : Master-slave
- AWS : MySQL backup & restore
- AWS RDS : Cross-Region Read Replicas for MySQL and Snapshots for PostgreSQL
- AWS : Restoring Postgres on EC2 instance from S3 backup
- AWS : Q & A
- AWS : Security
- AWS : Security groups vs. network ACLs
- AWS : Scaling-Up
- AWS : Networking
- AWS : Single Sign-on (SSO) with Okta
- AWS : JIT (Just-in-Time) with Okta
Ph.D. / Golden Gate Ave, San Francisco / Seoul National Univ / Carnegie Mellon / UC Berkeley / DevOps / Deep Learning / Visualization