Docker - Packer
The docker Packer builder builds Docker images using
Docker. The builder starts a Docker container, runs provisioners within this
container, then exports the container for reuse or commits the image.
Packer builds Docker containers without the use of
Dockerfiles. By not using
Dockerfiles, Packer is able to provision containers with portable scripts or
configuration management systems that are not tied to Docker in any way. It also
has a simple mental model: you provision containers much the same way you
provision a normal virtualized or dedicated server.
The Docker builder must run on a machine that has Docker Engine installed. Therefore the builder only works on machines that support Docker and does not support running on a Docker remote host.
Ref : Docker Packer Builder
Packer may be installed in several ways. But we'll use a precompiled binary.
Packer is currently packaged as a zip file. It does not seem that HashCorp has any near term plans to provide system packages.
Next, unzip the downloaded package into a directory where Packer will be installed: /usr/local/packer.
After installing Packer, verify the installation worked by opening a new command prompt or console, and checking that packer is available:
$ packer Usage: packer [--version] [--help][ ] Available commands are: build build image(s) from template fix fixes templates from old versions of packer inspect see components of a template validate check that a template is valid version Prints the Packer version
Our first image will be an Amazon EC2 AMI with the following JSON template from Build an Image (basic.json).
{
"variables": {
"aws_access_key": "{{env `AWS_ACCESS_KEY_ID`}}",
"aws_secret_key": "{{env `AWS_SECRET_ACCESS_KEY`}}"
},
"builders": [{
"type": "amazon-ebs",
"access_key": "{{user `aws_access_key`}}",
"secret_key": "{{user `aws_secret_key`}}",
"region": "us-east-1",
"source_ami_filter": {
"filters": {
"virtualization-type": "hvm",
"name": "ubuntu/images/*ubuntu-xenial-16.04-amd64-server-*",
"root-device-type": "ebs"
},
"owners": ["526262051452"],
"most_recent": true
},
"instance_type": "t2.micro",
"ssh_username": "ubuntu",
"ami_name": "packer-example {{timestamp}}"
}]
}
We're passing in aws_access_key and aws_secret_key as user variables, keeping our secret keys out of the template.
They default to empty values. Later, the variables are used within the builder we defined in order to configure the actual keys for the Amazon builder.
If the default value is null, then the user variable will be required. This means that the user must specify a value for this variable or template validation will fail.
User variables are used by calling the {{user}} function in the form of {{user `variable`}}. This function can be used in any value but type within the template: in builders, provisioners, anywhere outside the variables section.
Within the object, the builders section contains an array of JSON objects configuring a specific builder. A builder is a component of Packer that is responsible for creating a machine and turning that machine into an image.
The template will default "access_key" to be the value of the "aws_access_key", and "secret_key" to be the value of the "aws_secret_key" environment variables. To make this work, we may want to set the env variables unless we want to pass them in through the command line:
export AWS_ACCESS_KEY_ID=MYACCESSKEYID export AWS_SECRET_ACCESS_KEY=MYSECRETACCESSKEY
In our case, we're only configuring a single builder of type amazon-ebs. This is the Amazon EC2 AMI builder that ships with Packer. This builder builds an EBS-backed AMI by launching a source AMI, provisioning on top of that, and re-packaging it into a new AMI.
Before we take this template and build an image from it, let's validate the template by running packer validate basic.json. This command checks the syntax as well as the configuration values to verify they look valid. The output should look similar to below, because the template should be valid. If there are any errors, this command will tell us.
$ packer validate basic.json Template validated successfully.
Now that we validated template, it is time to build our first image. This is done by calling packer build with the template file. The output should look similar to below:
$ packer build basic.json
amazon-ebs output will be in this color.
==> amazon-ebs: Prevalidating AMI Name: packer-example 1539718379
amazon-ebs: Found Image ID: ami-0735ea082a1534cac
==> amazon-ebs: Creating temporary keypair: packer_5bc63ceb-8413-059c-bbb2-c6832f9399eb
==> amazon-ebs: Creating temporary security group for this instance: packer_5bc63cee-a934-c59a-1d52-7eb8d14ea5b9
==> amazon-ebs: Authorizing access to port 22 from 0.0.0.0/0 in the temporary security group...
==> amazon-ebs: Launching a source AWS instance...
==> amazon-ebs: Adding tags to source instance
amazon-ebs: Adding tag: "Name": "Packer Builder"
amazon-ebs: Instance ID: i-0ab0cd22ebe22f7dc
==> amazon-ebs: Waiting for instance (i-0ab0cd22ebe22f7dc) to become ready...
==> amazon-ebs: Using ssh communicator to connect: 52.23.153.69
==> amazon-ebs: Waiting for SSH to become available...
==> amazon-ebs: Connected to SSH!
==> amazon-ebs: Stopping the source instance...
amazon-ebs: Stopping instance, attempt 1
==> amazon-ebs: Waiting for the instance to stop...
==> amazon-ebs: Creating unencrypted AMI packer-example 1539718379 from instance i-0ab0cd22ebe22f7dc
amazon-ebs: AMI: ami-0fcee241ea83804cd
==> amazon-ebs: Waiting for AMI to become ready...
==> amazon-ebs: Terminating the source AWS instance...
==> amazon-ebs: Cleaning up any extra volumes...
==> amazon-ebs: No volumes to clean up, skipping
==> amazon-ebs: Deleting temporary security group...
==> amazon-ebs: Deleting temporary keypair...
Build 'amazon-ebs' finished.
==> Builds finished. The artifacts of successful builds are:
--> amazon-ebs: AMIs were created:
us-east-1: ami-0fcee241ea83804cd
We can see the AMI has been created with Packer. At the end of running packer build, Packer outputs the artifacts that were created as part of the build. In our example, we only have a single artifact: the AMI in us-east-1 that was created!
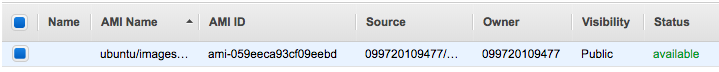
Let's create a txt file (welcome.txt):
WELCOME TO PACKER!
Then, create a script, basic2.sh:
!#/bin/bash echo "hello"
And updated template with provisioning, basic2.json:
{
"variables": {
"aws_access_key": "{{env `AWS_ACCESS_KEY_ID`}}",
"aws_secret_key": "{{env `AWS_SECRET_ACCESS_KEY`}}"
},
"builders": [{
"type": "amazon-ebs",
"access_key": "{{user `aws_access_key`}}",
"secret_key": "{{user `aws_secret_key`}}",
"region": "us-east-1",
"source_ami_filter": {
"filters": {
"virtualization-type": "hvm",
"name": "ubuntu/images/*ubuntu-xenial-16.04-amd64-server-*",
"root-device-type": "ebs"
},
"owners": ["099720109477"],
"most_recent": true
},
"instance_type": "t2.micro",
"ssh_username": "ubuntu",
"ami_name": "packer-example {{timestamp}}"
}],
"provisioners": [
{
"type": "file",
"source": "./welcome.txt",
"destination": "/home/ubuntu/"
},
{
"type": "shell",
"inline":[
"ls -al /home/ubuntu",
"cat /home/ubuntu/welcome.txt"
]
},
{
"type": "shell",
"script": "./basic2.sh"
}
]
}
The one provisioner we defined has a type of shell. This provisioner ships with Packer and runs shell scripts on the running machine.
Here are the files we have in the current directory:
$ ls basic.json basic2.json basic2.sh welcome.txt
To build, let's run packer build basic2.json, and our output will look like this:
$ packer build basic2.json
amazon-ebs output will be in this color.
==> amazon-ebs: Prevalidating AMI Name: packer-example 1539731390
amazon-ebs: Found Image ID: ami-0735ea082a1534cac
==> amazon-ebs: Creating temporary keypair: packer_5bc66fbe-4d49-c4ea-da79-f624f5c45cd1
==> amazon-ebs: Creating temporary security group for this instance: packer_5bc66fc1-9f71-5882-0241-39f52924b16f
==> amazon-ebs: Authorizing access to port 22 from 0.0.0.0/0 in the temporary security group...
==> amazon-ebs: Launching a source AWS instance...
==> amazon-ebs: Adding tags to source instance
amazon-ebs: Adding tag: "Name": "Packer Builder"
amazon-ebs: Instance ID: i-03ad86a5ec48b47c8
==> amazon-ebs: Waiting for instance (i-03ad86a5ec48b47c8) to become ready...
==> amazon-ebs: Using ssh communicator to connect: 34.207.141.216
==> amazon-ebs: Waiting for SSH to become available...
==> amazon-ebs: Connected to SSH!
==> amazon-ebs: Uploading ./welcome.txt => /home/ubuntu/
1 items: 19 B / 19 B [==================================================================================================================================] 0s
==> amazon-ebs: Provisioning with shell script: /var/folders/3s/42rgkz495lj4ydjgnqhxn_400000gn/T/packer-shell008618527
amazon-ebs: total 32
amazon-ebs: drwxr-xr-x 4 ubuntu ubuntu 4096 Oct 16 23:10 .
amazon-ebs: drwxr-xr-x 3 root root 4096 Oct 16 23:10 ..
amazon-ebs: -rw-r--r-- 1 ubuntu ubuntu 220 Aug 31 2015 .bash_logout
amazon-ebs: -rw-r--r-- 1 ubuntu ubuntu 3771 Aug 31 2015 .bashrc
amazon-ebs: drwx------ 2 ubuntu ubuntu 4096 Oct 16 23:10 .cache
amazon-ebs: -rw-r--r-- 1 ubuntu ubuntu 655 May 16 2017 .profile
amazon-ebs: drwx------ 2 ubuntu ubuntu 4096 Oct 16 23:10 .ssh
amazon-ebs: -rw-r--r-- 1 ubuntu ubuntu 19 Oct 16 23:10 welcome.txt
amazon-ebs: WELCOME TO PACKER!
==> amazon-ebs: Provisioning with shell script: ./basic2.sh
amazon-ebs: hello
==> amazon-ebs: Stopping the source instance...
amazon-ebs: Stopping instance, attempt 1
==> amazon-ebs: Waiting for the instance to stop...
==> amazon-ebs: Creating unencrypted AMI packer-example 1539731390 from instance i-03ad86a5ec48b47c8
amazon-ebs: AMI: ami-072d5b06d247566da
==> amazon-ebs: Waiting for AMI to become ready...
==> amazon-ebs: Terminating the source AWS instance...
==> amazon-ebs: Cleaning up any extra volumes...
==> amazon-ebs: No volumes to clean up, skipping
==> amazon-ebs: Deleting temporary security group...
==> amazon-ebs: Deleting temporary keypair...
Build 'amazon-ebs' finished.
==> Builds finished. The artifacts of successful builds are:
--> amazon-ebs: AMIs were created:
us-east-1: ami-072d5b06d247566da
We created our first image with Packer. The image we just built, however, was basically just a repackaging of a previously existing base AMI. The real utility of Packer comes from being able to install and configure software into the images as well. This stage is also known as the provision step. Packer fully supports automated provisioning in order to install software onto the machines prior to turning them into images.
In this section, we're going to complete our image by installing Redis on it. This way, the image we end up building actually contains Redis pre-installed.
{
"variables": {
"aws_access_key": "{{env `AWS_ACCESS_KEY_ID`}}",
"aws_secret_key": "{{env `AWS_SECRET_ACCESS_KEY`}}"
},
"builders": [{
"type": "amazon-ebs",
"access_key": "{{user `aws_access_key`}}",
"secret_key": "{{user `aws_secret_key`}}",
"region": "us-east-1",
"source_ami_filter": {
"filters": {
"virtualization-type": "hvm",
"name": "ubuntu/images/*ubuntu-xenial-16.04-amd64-server-*",
"root-device-type": "ebs"
},
"owners": ["099720109477"],
"most_recent": true
},
"instance_type": "t2.micro",
"ssh_username": "ubuntu",
"ami_name": "packer-example {{timestamp}}"
}],
"provisioners": [{
"type": "shell",
"inline": [
"sleep 30",
"sudo apt-get update",
"sudo apt-get install -y redis-server"
]
}]
}
To configure the provisioners, we added a new section provisioners to the template, alongside the builders configuration. The provisioners section is an array of provisioners to run. If multiple provisioners are specified, they are run in the order given.
By default, each provisioner is run for every builder defined.
Run:
$ packer build basic3.json
amazon-ebs output will be in this color.
==> amazon-ebs: Prevalidating AMI Name: packer-example 1539732516
amazon-ebs: Found Image ID: ami-0735ea082a1534cac
==> amazon-ebs: Creating temporary keypair: packer_5bc67424-a84b-097b-bcb6-73ebdc72217e
==> amazon-ebs: Creating temporary security group for this instance: packer_5bc67427-6b23-9264-39e4-c66a1864fbac
==> amazon-ebs: Authorizing access to port 22 from 0.0.0.0/0 in the temporary security group...
==> amazon-ebs: Launching a source AWS instance...
==> amazon-ebs: Adding tags to source instance
amazon-ebs: Adding tag: "Name": "Packer Builder"
amazon-ebs: Instance ID: i-02d9d633d15d3613a
==> amazon-ebs: Waiting for instance (i-02d9d633d15d3613a) to become ready...
==> amazon-ebs: Using ssh communicator to connect: 54.157.134.226
==> amazon-ebs: Waiting for SSH to become available...
==> amazon-ebs: Connected to SSH!
==> amazon-ebs: Provisioning with shell script: /var/folders/3s/42rgkz495lj4ydjgnqhxn_400000gn/T/packer-shell453321574
amazon-ebs: Hit:1 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial InRelease
amazon-ebs: Get:2 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates InRelease [109 kB]
amazon-ebs: Get:3 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports InRelease [107 kB]
amazon-ebs: Get:4 http://security.ubuntu.com/ubuntu xenial-security InRelease [107 kB]
amazon-ebs: Get:5 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/main Sources [868 kB]
amazon-ebs: Get:6 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/restricted Sources [4,808 B]
amazon-ebs: Get:7 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/universe Sources [7,728 kB]
amazon-ebs: Get:8 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/multiverse Sources [179 kB]
amazon-ebs: Get:9 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/universe amd64 Packages [7,532 kB]
amazon-ebs: Get:10 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/universe Translation-en [4,354 kB]
amazon-ebs: Get:11 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/multiverse amd64 Packages [144 kB]
amazon-ebs: Get:12 http://security.ubuntu.com/ubuntu xenial-security/main Sources [135 kB]
amazon-ebs: Get:13 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/multiverse Translation-en [106 kB]
amazon-ebs: Get:14 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/main Sources [322 kB]
amazon-ebs: Get:15 http://security.ubuntu.com/ubuntu xenial-security/restricted Sources [2,116 B]
amazon-ebs: Get:16 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/restricted Sources [2,528 B]
amazon-ebs: Get:17 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/universe Sources [224 kB]
amazon-ebs: Get:18 http://security.ubuntu.com/ubuntu xenial-security/universe Sources [78.4 kB]
amazon-ebs: Get:19 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/multiverse Sources [8,384 B]
amazon-ebs: Get:20 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/main amd64 Packages [860 kB]
amazon-ebs: Get:21 http://security.ubuntu.com/ubuntu xenial-security/multiverse Sources [2,088 B]
amazon-ebs: Get:22 http://security.ubuntu.com/ubuntu xenial-security/main amd64 Packages [568 kB]
amazon-ebs: Get:23 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/main Translation-en [351 kB]
amazon-ebs: Get:24 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/universe amd64 Packages [694 kB]
amazon-ebs: Get:25 http://security.ubuntu.com/ubuntu xenial-security/main Translation-en [238 kB]
amazon-ebs: Get:26 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/universe Translation-en [280 kB]
amazon-ebs: Get:27 http://security.ubuntu.com/ubuntu xenial-security/universe amd64 Packages [391 kB]
amazon-ebs: Get:28 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/multiverse amd64 Packages [16.4 kB]
amazon-ebs: Get:29 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/multiverse Translation-en [8,344 B]
amazon-ebs: Get:30 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports/main Sources [4,868 B]
amazon-ebs: Get:31 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports/universe Sources [6,740 B]
amazon-ebs: Get:32 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports/main amd64 Packages [7,304 B]
amazon-ebs: Get:33 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports/main Translation-en [4,456 B]
amazon-ebs: Get:34 http://security.ubuntu.com/ubuntu xenial-security/universe Translation-en [149 kB]
amazon-ebs: Get:35 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports/universe amd64 Packages [7,804 B]
amazon-ebs: Get:36 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports/universe Translation-en [4,184 B]
amazon-ebs: Get:37 http://security.ubuntu.com/ubuntu xenial-security/multiverse amd64 Packages [3,460 B]
amazon-ebs: Get:38 http://security.ubuntu.com/ubuntu xenial-security/multiverse Translation-en [1,744 B]
amazon-ebs: Fetched 25.6 MB in 4s (5,380 kB/s)
amazon-ebs: Reading package lists...
amazon-ebs: Reading package lists...
amazon-ebs: Building dependency tree...
amazon-ebs: Reading state information...
amazon-ebs: The following additional packages will be installed:
amazon-ebs: libjemalloc1 redis-tools
amazon-ebs: Suggested packages:
amazon-ebs: ruby-redis
amazon-ebs: The following NEW packages will be installed:
amazon-ebs: libjemalloc1 redis-server redis-tools
amazon-ebs: 0 upgraded, 3 newly installed, 0 to remove and 1 not upgraded.
amazon-ebs: Need to get 517 kB of archives.
amazon-ebs: After this operation, 1,505 kB of additional disk space will be used.
amazon-ebs: Get:1 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/universe amd64 libjemalloc1 amd64 3.6.0-9ubuntu1 [78.9 kB]
amazon-ebs: Get:2 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/universe amd64 redis-tools amd64 2:3.0.6-1 [95.3 kB]
amazon-ebs: Get:3 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/universe amd64 redis-server amd64 2:3.0.6-1 [343 kB]
amazon-ebs: debconf: unable to initialize frontend: Dialog
amazon-ebs: debconf: (Dialog frontend will not work on a dumb terminal, an emacs shell buffer, or without a controlling terminal.)
amazon-ebs: debconf: falling back to frontend: Readline
amazon-ebs: debconf: unable to initialize frontend: Readline
amazon-ebs: debconf: (This frontend requires a controlling tty.)
amazon-ebs: debconf: falling back to frontend: Teletype
amazon-ebs: dpkg-preconfigure: unable to re-open stdin:
amazon-ebs: Fetched 517 kB in 0s (12.0 MB/s)
amazon-ebs: Selecting previously unselected package libjemalloc1.
amazon-ebs: (Reading database ... 51287 files and directories currently installed.)
amazon-ebs: Preparing to unpack .../libjemalloc1_3.6.0-9ubuntu1_amd64.deb ...
amazon-ebs: Unpacking libjemalloc1 (3.6.0-9ubuntu1) ...
amazon-ebs: Selecting previously unselected package redis-tools.
amazon-ebs: Preparing to unpack .../redis-tools_2%3a3.0.6-1_amd64.deb ...
amazon-ebs: Unpacking redis-tools (2:3.0.6-1) ...
amazon-ebs: Selecting previously unselected package redis-server.
amazon-ebs: Preparing to unpack .../redis-server_2%3a3.0.6-1_amd64.deb ...
amazon-ebs: Unpacking redis-server (2:3.0.6-1) ...
amazon-ebs: Processing triggers for libc-bin (2.23-0ubuntu10) ...
amazon-ebs: Processing triggers for man-db (2.7.5-1) ...
amazon-ebs: Processing triggers for systemd (229-4ubuntu21.4) ...
amazon-ebs: Processing triggers for ureadahead (0.100.0-19) ...
amazon-ebs: Setting up libjemalloc1 (3.6.0-9ubuntu1) ...
amazon-ebs: Setting up redis-tools (2:3.0.6-1) ...
amazon-ebs: Setting up redis-server (2:3.0.6-1) ...
amazon-ebs: Processing triggers for libc-bin (2.23-0ubuntu10) ...
amazon-ebs: Processing triggers for systemd (229-4ubuntu21.4) ...
amazon-ebs: Processing triggers for ureadahead (0.100.0-19) ...
==> amazon-ebs: Stopping the source instance...
amazon-ebs: Stopping instance, attempt 1
==> amazon-ebs: Waiting for the instance to stop...
==> amazon-ebs: Creating unencrypted AMI packer-example 1539732516 from instance i-02d9d633d15d3613a
amazon-ebs: AMI: ami-098058a07624e33c4
==> amazon-ebs: Waiting for AMI to become ready...
==> amazon-ebs: Terminating the source AWS instance...
==> amazon-ebs: Cleaning up any extra volumes...
==> amazon-ebs: No volumes to clean up, skipping
==> amazon-ebs: Deleting temporary security group...
==> amazon-ebs: Deleting temporary keypair...
Build 'amazon-ebs' finished.
==> Builds finished. The artifacts of successful builds are:
--> amazon-ebs: AMIs were created:
us-east-1: ami-098058a07624e33c4
We're enabling a single post-processor named "vagrant". The post-processor is built-in to Packer and will create Vagrant boxes.
{
"variables": {
"aws_access_key": "{{env `AWS_ACCESS_KEY_ID`}}",
"aws_secret_key": "{{env `AWS_SECRET_ACCESS_KEY`}}"
},
"builders": [{
"type": "amazon-ebs",
"access_key": "{{user `aws_access_key`}}",
"secret_key": "{{user `aws_secret_key`}}",
"region": "us-east-1",
"source_ami_filter": {
"filters": {
"virtualization-type": "hvm",
"name": "ubuntu/images/*ubuntu-xenial-16.04-amd64-server-*",
"root-device-type": "ebs"
},
"owners": ["099720109477"],
"most_recent": true
},
"instance_type": "t2.micro",
"ssh_username": "ubuntu",
"ami_name": "packer-example {{timestamp}}"
}],
"provisioners": [{
"type": "shell",
"inline": [
"sleep 30",
"sudo apt-get update",
"sudo apt-get install -y redis-server"
]
}],
"post-processors": ["vagrant"]
}
We just run a normal packer build and it will now use the post-processor. We're passing the -only=amazon-ebs flag to packer build so it only builds the AMI. The command should look like the following:
$ packer build -only=amazon-ebs basic4.json
amazon-ebs output will be in this color.
==> amazon-ebs: Prevalidating AMI Name: packer-example 1539744373
amazon-ebs: Found Image ID: ami-0735ea082a1534cac
==> amazon-ebs: Creating temporary keypair: packer_5bc6a275-dffb-8b58-ed87-9c3722cb9250
==> amazon-ebs: Creating temporary security group for this instance: packer_5bc6a278-6b86-a8ad-c87a-a94cb3d21097
==> amazon-ebs: Authorizing access to port 22 from 0.0.0.0/0 in the temporary security group...
==> amazon-ebs: Launching a source AWS instance...
==> amazon-ebs: Adding tags to source instance
amazon-ebs: Adding tag: "Name": "Packer Builder"
amazon-ebs: Instance ID: i-08087dd30089d1868
==> amazon-ebs: Waiting for instance (i-08087dd30089d1868) to become ready...
==> amazon-ebs: Using ssh communicator to connect: 107.21.90.213
==> amazon-ebs: Waiting for SSH to become available...
==> amazon-ebs: Connected to SSH!
==> amazon-ebs: Provisioning with shell script: /var/folders/3s/42rgkz495lj4ydjgnqhxn_400000gn/T/packer-shell085116188
amazon-ebs: Hit:1 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial InRelease
amazon-ebs: Get:2 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates InRelease [109 kB]
amazon-ebs: Get:3 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports InRelease [107 kB]
amazon-ebs: Get:4 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/main Sources [868 kB]
amazon-ebs: Get:5 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/restricted Sources [4,808 B]
amazon-ebs: Get:6 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/universe Sources [7,728 kB]
amazon-ebs: Get:7 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/multiverse Sources [179 kB]
amazon-ebs: Get:8 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/universe amd64 Packages [7,532 kB]
amazon-ebs: Get:9 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/universe Translation-en [4,354 kB]
amazon-ebs: Get:10 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/multiverse amd64 Packages [144 kB]
amazon-ebs: Get:11 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/multiverse Translation-en [106 kB]
amazon-ebs: Get:12 http://security.ubuntu.com/ubuntu xenial-security InRelease [107 kB]
amazon-ebs: Get:13 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/main Sources [322 kB]
amazon-ebs: Get:14 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/restricted Sources [2,528 B]
amazon-ebs: Get:15 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/universe Sources [224 kB]
amazon-ebs: Get:16 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/multiverse Sources [8,384 B]
amazon-ebs: Get:17 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/main amd64 Packages [860 kB]
amazon-ebs: Get:18 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/main Translation-en [351 kB]
amazon-ebs: Get:19 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/universe amd64 Packages [694 kB]
amazon-ebs: Get:20 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/universe Translation-en [280 kB]
amazon-ebs: Get:21 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/multiverse amd64 Packages [16.4 kB]
amazon-ebs: Get:22 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-updates/multiverse Translation-en [8,344 B]
amazon-ebs: Get:23 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports/main Sources [4,868 B]
amazon-ebs: Get:24 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports/universe Sources [6,740 B]
amazon-ebs: Get:25 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports/main amd64 Packages [7,304 B]
amazon-ebs: Get:26 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports/main Translation-en [4,456 B]
amazon-ebs: Get:27 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports/universe amd64 Packages [7,804 B]
amazon-ebs: Get:28 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial-backports/universe Translation-en [4,184 B]
amazon-ebs: Get:29 http://security.ubuntu.com/ubuntu xenial-security/main Sources [135 kB]
amazon-ebs: Get:30 http://security.ubuntu.com/ubuntu xenial-security/restricted Sources [2,116 B]
amazon-ebs: Get:31 http://security.ubuntu.com/ubuntu xenial-security/universe Sources [78.4 kB]
amazon-ebs: Get:32 http://security.ubuntu.com/ubuntu xenial-security/multiverse Sources [2,088 B]
amazon-ebs: Get:33 http://security.ubuntu.com/ubuntu xenial-security/main amd64 Packages [568 kB]
amazon-ebs: Get:34 http://security.ubuntu.com/ubuntu xenial-security/main Translation-en [238 kB]
amazon-ebs: Get:35 http://security.ubuntu.com/ubuntu xenial-security/universe amd64 Packages [391 kB]
amazon-ebs: Get:36 http://security.ubuntu.com/ubuntu xenial-security/universe Translation-en [149 kB]
amazon-ebs: Get:37 http://security.ubuntu.com/ubuntu xenial-security/multiverse amd64 Packages [3,460 B]
amazon-ebs: Get:38 http://security.ubuntu.com/ubuntu xenial-security/multiverse Translation-en [1,744 B]
amazon-ebs: Fetched 25.6 MB in 4s (5,541 kB/s)
amazon-ebs: Reading package lists...
amazon-ebs: Reading package lists...
amazon-ebs: Building dependency tree...
amazon-ebs: Reading state information...
amazon-ebs: The following additional packages will be installed:
amazon-ebs: libjemalloc1 redis-tools
amazon-ebs: Suggested packages:
amazon-ebs: ruby-redis
amazon-ebs: The following NEW packages will be installed:
amazon-ebs: libjemalloc1 redis-server redis-tools
amazon-ebs: 0 upgraded, 3 newly installed, 0 to remove and 1 not upgraded.
amazon-ebs: Need to get 517 kB of archives.
amazon-ebs: After this operation, 1,505 kB of additional disk space will be used.
amazon-ebs: Get:1 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/universe amd64 libjemalloc1 amd64 3.6.0-9ubuntu1 [78.9 kB]
amazon-ebs: Get:2 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/universe amd64 redis-tools amd64 2:3.0.6-1 [95.3 kB]
amazon-ebs: Get:3 http://us-east-1.ec2.archive.ubuntu.com/ubuntu xenial/universe amd64 redis-server amd64 2:3.0.6-1 [343 kB]
amazon-ebs: debconf: unable to initialize frontend: Dialog
amazon-ebs: debconf: (Dialog frontend will not work on a dumb terminal, an emacs shell buffer, or without a controlling terminal.)
amazon-ebs: debconf: falling back to frontend: Readline
amazon-ebs: Fetched 517 kB in 0s (14.4 MB/s)
amazon-ebs: debconf: unable to initialize frontend: Readline
amazon-ebs: debconf: (This frontend requires a controlling tty.)
amazon-ebs: debconf: falling back to frontend: Teletype
amazon-ebs: dpkg-preconfigure: unable to re-open stdin:
amazon-ebs: Selecting previously unselected package libjemalloc1.
amazon-ebs: (Reading database ... 51287 files and directories currently installed.)
amazon-ebs: Preparing to unpack .../libjemalloc1_3.6.0-9ubuntu1_amd64.deb ...
amazon-ebs: Unpacking libjemalloc1 (3.6.0-9ubuntu1) ...
amazon-ebs: Selecting previously unselected package redis-tools.
amazon-ebs: Preparing to unpack .../redis-tools_2%3a3.0.6-1_amd64.deb ...
amazon-ebs: Unpacking redis-tools (2:3.0.6-1) ...
amazon-ebs: Selecting previously unselected package redis-server.
amazon-ebs: Preparing to unpack .../redis-server_2%3a3.0.6-1_amd64.deb ...
amazon-ebs: Unpacking redis-server (2:3.0.6-1) ...
amazon-ebs: Processing triggers for libc-bin (2.23-0ubuntu10) ...
amazon-ebs: Processing triggers for man-db (2.7.5-1) ...
amazon-ebs: Processing triggers for systemd (229-4ubuntu21.4) ...
amazon-ebs: Processing triggers for ureadahead (0.100.0-19) ...
amazon-ebs: Setting up libjemalloc1 (3.6.0-9ubuntu1) ...
amazon-ebs: Setting up redis-tools (2:3.0.6-1) ...
amazon-ebs: Setting up redis-server (2:3.0.6-1) ...
amazon-ebs: Processing triggers for libc-bin (2.23-0ubuntu10) ...
amazon-ebs: Processing triggers for systemd (229-4ubuntu21.4) ...
amazon-ebs: Processing triggers for ureadahead (0.100.0-19) ...
==> amazon-ebs: Stopping the source instance...
amazon-ebs: Stopping instance, attempt 1
==> amazon-ebs: Waiting for the instance to stop...
==> amazon-ebs: Creating unencrypted AMI packer-example 1539744373 from instance i-08087dd30089d1868
amazon-ebs: AMI: ami-061f369cce5a6ee90
==> amazon-ebs: Waiting for AMI to become ready...
==> amazon-ebs: Terminating the source AWS instance...
==> amazon-ebs: Cleaning up any extra volumes...
==> amazon-ebs: No volumes to clean up, skipping
==> amazon-ebs: Deleting temporary security group...
==> amazon-ebs: Deleting temporary keypair...
==> amazon-ebs: Running post-processor: vagrant
==> amazon-ebs (vagrant): Creating Vagrant box for 'aws' provider
amazon-ebs (vagrant): Compressing: Vagrantfile
amazon-ebs (vagrant): Compressing: metadata.json
Build 'amazon-ebs' finished.
==> Builds finished. The artifacts of successful builds are:
--> amazon-ebs: AMIs were created:
us-east-1: ami-061f369cce5a6ee90
--> amazon-ebs: 'aws' provider box: packer_amazon-ebs_aws.box
Notice at the end in the artifact listing that a Vagrant box was made in the current directory. Note also that when using post-processors, Vagrant removes intermediary artifacts since they're usually not wanted. Only the final artifact is preserved.
Docker & K8s
- Docker install on Amazon Linux AMI
- Docker install on EC2 Ubuntu 14.04
- Docker container vs Virtual Machine
- Docker install on Ubuntu 14.04
- Docker Hello World Application
- Nginx image - share/copy files, Dockerfile
- Working with Docker images : brief introduction
- Docker image and container via docker commands (search, pull, run, ps, restart, attach, and rm)
- More on docker run command (docker run -it, docker run --rm, etc.)
- Docker Networks - Bridge Driver Network
- Docker Persistent Storage
- File sharing between host and container (docker run -d -p -v)
- Linking containers and volume for datastore
- Dockerfile - Build Docker images automatically I - FROM, MAINTAINER, and build context
- Dockerfile - Build Docker images automatically II - revisiting FROM, MAINTAINER, build context, and caching
- Dockerfile - Build Docker images automatically III - RUN
- Dockerfile - Build Docker images automatically IV - CMD
- Dockerfile - Build Docker images automatically V - WORKDIR, ENV, ADD, and ENTRYPOINT
- Docker - Apache Tomcat
- Docker - NodeJS
- Docker - NodeJS with hostname
- Docker Compose - NodeJS with MongoDB
- Docker - Prometheus and Grafana with Docker-compose
- Docker - StatsD/Graphite/Grafana
- Docker - Deploying a Java EE JBoss/WildFly Application on AWS Elastic Beanstalk Using Docker Containers
- Docker : NodeJS with GCP Kubernetes Engine
- Docker : Jenkins Multibranch Pipeline with Jenkinsfile and Github
- Docker : Jenkins Master and Slave
- Docker - ELK : ElasticSearch, Logstash, and Kibana
- Docker - ELK 7.6 : Elasticsearch on Centos 7
- Docker - ELK 7.6 : Filebeat on Centos 7
- Docker - ELK 7.6 : Logstash on Centos 7
- Docker - ELK 7.6 : Kibana on Centos 7
- Docker - ELK 7.6 : Elastic Stack with Docker Compose
- Docker - Deploy Elastic Cloud on Kubernetes (ECK) via Elasticsearch operator on minikube
- Docker - Deploy Elastic Stack via Helm on minikube
- Docker Compose - A gentle introduction with WordPress
- Docker Compose - MySQL
- MEAN Stack app on Docker containers : micro services
- MEAN Stack app on Docker containers : micro services via docker-compose
- Docker Compose - Hashicorp's Vault and Consul Part A (install vault, unsealing, static secrets, and policies)
- Docker Compose - Hashicorp's Vault and Consul Part B (EaaS, dynamic secrets, leases, and revocation)
- Docker Compose - Hashicorp's Vault and Consul Part C (Consul)
- Docker Compose with two containers - Flask REST API service container and an Apache server container
- Docker compose : Nginx reverse proxy with multiple containers
- Docker & Kubernetes : Envoy - Getting started
- Docker & Kubernetes : Envoy - Front Proxy
- Docker & Kubernetes : Ambassador - Envoy API Gateway on Kubernetes
- Docker Packer
- Docker Cheat Sheet
- Docker Q & A #1
- Kubernetes Q & A - Part I
- Kubernetes Q & A - Part II
- Docker - Run a React app in a docker
- Docker - Run a React app in a docker II (snapshot app with nginx)
- Docker - NodeJS and MySQL app with React in a docker
- Docker - Step by Step NodeJS and MySQL app with React - I
- Installing LAMP via puppet on Docker
- Docker install via Puppet
- Nginx Docker install via Ansible
- Apache Hadoop CDH 5.8 Install with QuickStarts Docker
- Docker - Deploying Flask app to ECS
- Docker Compose - Deploying WordPress to AWS
- Docker - WordPress Deploy to ECS with Docker-Compose (ECS-CLI EC2 type)
- Docker - WordPress Deploy to ECS with Docker-Compose (ECS-CLI Fargate type)
- Docker - ECS Fargate
- Docker - AWS ECS service discovery with Flask and Redis
- Docker & Kubernetes : minikube
- Docker & Kubernetes 2 : minikube Django with Postgres - persistent volume
- Docker & Kubernetes 3 : minikube Django with Redis and Celery
- Docker & Kubernetes 4 : Django with RDS via AWS Kops
- Docker & Kubernetes : Kops on AWS
- Docker & Kubernetes : Ingress controller on AWS with Kops
- Docker & Kubernetes : HashiCorp's Vault and Consul on minikube
- Docker & Kubernetes : HashiCorp's Vault and Consul - Auto-unseal using Transit Secrets Engine
- Docker & Kubernetes : Persistent Volumes & Persistent Volumes Claims - hostPath and annotations
- Docker & Kubernetes : Persistent Volumes - Dynamic volume provisioning
- Docker & Kubernetes : DaemonSet
- Docker & Kubernetes : Secrets
- Docker & Kubernetes : kubectl command
- Docker & Kubernetes : Assign a Kubernetes Pod to a particular node in a Kubernetes cluster
- Docker & Kubernetes : Configure a Pod to Use a ConfigMap
- AWS : EKS (Elastic Container Service for Kubernetes)
- Docker & Kubernetes : Run a React app in a minikube
- Docker & Kubernetes : Minikube install on AWS EC2
- Docker & Kubernetes : Cassandra with a StatefulSet
- Docker & Kubernetes : Terraform and AWS EKS
- Docker & Kubernetes : Pods and Service definitions
- Docker & Kubernetes : Service IP and the Service Type
- Docker & Kubernetes : Kubernetes DNS with Pods and Services
- Docker & Kubernetes : Headless service and discovering pods
- Docker & Kubernetes : Scaling and Updating application
- Docker & Kubernetes : Horizontal pod autoscaler on minikubes
- Docker & Kubernetes : From a monolithic app to micro services on GCP Kubernetes
- Docker & Kubernetes : Rolling updates
- Docker & Kubernetes : Deployments to GKE (Rolling update, Canary and Blue-green deployments)
- Docker & Kubernetes : Slack Chat Bot with NodeJS on GCP Kubernetes
- Docker & Kubernetes : Continuous Delivery with Jenkins Multibranch Pipeline for Dev, Canary, and Production Environments on GCP Kubernetes
- Docker & Kubernetes : NodePort vs LoadBalancer vs Ingress
- Docker & Kubernetes : MongoDB / MongoExpress on Minikube
- Docker & Kubernetes : Load Testing with Locust on GCP Kubernetes
- Docker & Kubernetes : MongoDB with StatefulSets on GCP Kubernetes Engine
- Docker & Kubernetes : Nginx Ingress Controller on Minikube
- Docker & Kubernetes : Setting up Ingress with NGINX Controller on Minikube (Mac)
- Docker & Kubernetes : Nginx Ingress Controller for Dashboard service on Minikube
- Docker & Kubernetes : Nginx Ingress Controller on GCP Kubernetes
- Docker & Kubernetes : Kubernetes Ingress with AWS ALB Ingress Controller in EKS
- Docker & Kubernetes : Setting up a private cluster on GCP Kubernetes
- Docker & Kubernetes : Kubernetes Namespaces (default, kube-public, kube-system) and switching namespaces (kubens)
- Docker & Kubernetes : StatefulSets on minikube
- Docker & Kubernetes : RBAC
- Docker & Kubernetes Service Account, RBAC, and IAM
- Docker & Kubernetes - Kubernetes Service Account, RBAC, IAM with EKS ALB, Part 1
- Docker & Kubernetes : Helm Chart
- Docker & Kubernetes : My first Helm deploy
- Docker & Kubernetes : Readiness and Liveness Probes
- Docker & Kubernetes : Helm chart repository with Github pages
- Docker & Kubernetes : Deploying WordPress and MariaDB with Ingress to Minikube using Helm Chart
- Docker & Kubernetes : Deploying WordPress and MariaDB to AWS using Helm 2 Chart
- Docker & Kubernetes : Deploying WordPress and MariaDB to AWS using Helm 3 Chart
- Docker & Kubernetes : Helm Chart for Node/Express and MySQL with Ingress
- Docker & Kubernetes : Deploy Prometheus and Grafana using Helm and Prometheus Operator - Monitoring Kubernetes node resources out of the box
- Docker & Kubernetes : Deploy Prometheus and Grafana using kube-prometheus-stack Helm Chart
- Docker & Kubernetes : Istio (service mesh) sidecar proxy on GCP Kubernetes
- Docker & Kubernetes : Istio on EKS
- Docker & Kubernetes : Istio on Minikube with AWS EC2 for Bookinfo Application
- Docker & Kubernetes : Deploying .NET Core app to Kubernetes Engine and configuring its traffic managed by Istio (Part I)
- Docker & Kubernetes : Deploying .NET Core app to Kubernetes Engine and configuring its traffic managed by Istio (Part II - Prometheus, Grafana, pin a service, split traffic, and inject faults)
- Docker & Kubernetes : Helm Package Manager with MySQL on GCP Kubernetes Engine
- Docker & Kubernetes : Deploying Memcached on Kubernetes Engine
- Docker & Kubernetes : EKS Control Plane (API server) Metrics with Prometheus
- Docker & Kubernetes : Spinnaker on EKS with Halyard
- Docker & Kubernetes : Continuous Delivery Pipelines with Spinnaker and Kubernetes Engine
- Docker & Kubernetes : Multi-node Local Kubernetes cluster : Kubeadm-dind (docker-in-docker)
- Docker & Kubernetes : Multi-node Local Kubernetes cluster : Kubeadm-kind (k8s-in-docker)
- Docker & Kubernetes : nodeSelector, nodeAffinity, taints/tolerations, pod affinity and anti-affinity - Assigning Pods to Nodes
- Docker & Kubernetes : Jenkins-X on EKS
- Docker & Kubernetes : ArgoCD App of Apps with Heml on Kubernetes
- Docker & Kubernetes : ArgoCD on Kubernetes cluster
- Docker & Kubernetes : GitOps with ArgoCD for Continuous Delivery to Kubernetes clusters (minikube) - guestbook
Ph.D. / Golden Gate Ave, San Francisco / Seoul National Univ / Carnegie Mellon / UC Berkeley / DevOps / Deep Learning / Visualization