Docker & Kubernetes: Istio on Minikube with AWS EC2 for Bookinfo Application
We're going to install Minikube on Amazon Linux 2 (t2.xlarge):
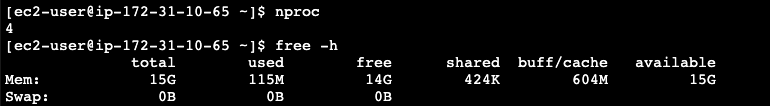
To install Minikube follow these steps:
- Install Docker:
$ sudo yum install -y docker ... Installed: docker.x86_64 0:20.10.25-1.amzn2.0.3 Dependency Installed: containerd.x86_64 0:1.6.19-1.amzn2.0.5 libcgroup.x86_64 0:0.41-21.amzn2 pigz.x86_64 0:2.3.4-1.amzn2.0.1 runc.x86_64 0:1.1.7-4.amzn2 Complete! $ sudo systemctl enable docker Created symlink from /etc/systemd/system/multi-user.target.wants/docker.service to /usr/lib/systemd/system/docker.service. $ sudo systemctl start docker
- Install Kubectl:
$ curl -LO "https://dl.k8s.io/release/$(curl -L -s https://dl.k8s.io/release/stable.txt)/bin/linux/amd64/kubectl" $ chmod +x kubectl $ sudo mv ./kubectl /usr/local/bin/kubectl $ which kubectl /usr/local/bin/kubectl
- Download Minikube:
$ curl -Lo minikube https://storage.googleapis.com/minikube/releases/latest/minikube-linux-amd64 $ chmod +x minikube
- Move Minikube to the binary path:
$ sudo mv ./minikube /usr/local/bin/minikube $ minikube version minikube version: v1.31.2
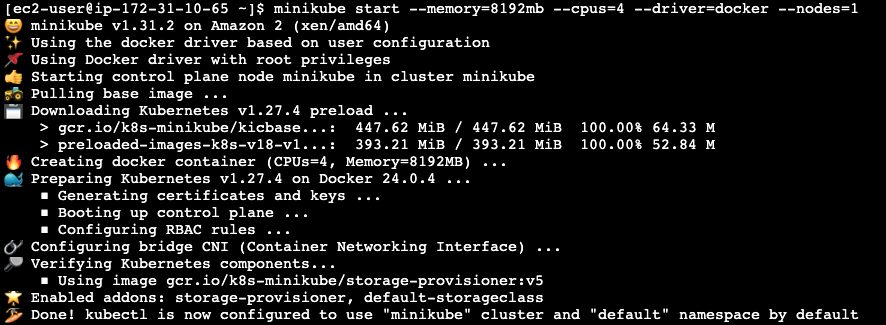
- Start Minikube: Make sure to start minikube with at least 8192 MB of memory and 4 CPUs
$ sudo usermod -aG docker $USER && newgrp docker $ groups ec2-user ec2-user : ec2-user adm wheel systemd-journal docker $ minikube start --memory=8192mb --cpus=4 --driver=docker --nodes=1
- Verify Minikube is running:
$ kubectl get nodes NAME STATUS ROLES AGE VERSION minikube Ready control-plane 2m36s v1.27.4
We should see a list of nodes, including one named minikube. This indicates that Minikube is running successfully.
We do not have to install Istio if we do minikube addons enable istio-provisioner; minikube addons enable istio.
These commands will enable the Istio addon on our Minikube cluster, which will install all of the necessary Istio components and configure them to work with our cluster.
- Enable istio addon:
$ minikube addons enable istio-provisioner The 'istio-provisioner' addon is enabled $ minikube addons enable istio The 'istio' addon is enabled
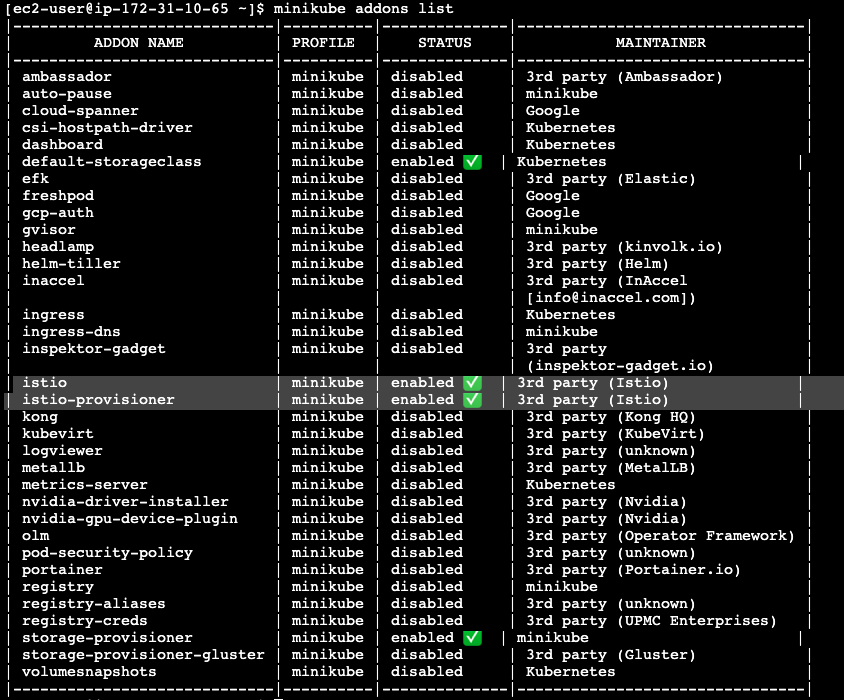 The istio-provisioner addon is responsible for provisioning Istio resources, such as sidecars and VirtualServices.
The istio addon is responsible for installing the Istio control plane components, such as the Pilot and Mixer.
The istio-provisioner addon is responsible for provisioning Istio resources, such as sidecars and VirtualServices.
The istio addon is responsible for installing the Istio control plane components, such as the Pilot and Mixer.
- Testing installation: we could run
kubectl get po -n istio-systemto see the progress for istio installation.$ kubectl get po -n istio-system
If everything went well we shouldn't get any errors about istio being installed in our cluster. - Disable istio:
$ minikube addons disable istio-provisioner $ minikube addons disable istio
- download and deploy the latest Istio resources :
$ curl -L https://git.io/getLatestIstio | sh - % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 100 4899 100 4899 0 0 6789 0 --:--:-- --:--:-- --:--:-- 6789 Downloading istio-1.19.3 from https://github.com/istio/istio/releases/download/1.19.3/istio-1.19.3-linux-amd64.tar.gz ... Istio 1.19.3 Download Complete! Istio has been successfully downloaded into the istio-1.19.3 folder on your system. Next Steps: See https://istio.io/latest/docs/setup/install/ to add Istio to your Kubernetes cluster. To configure the istioctl client tool for your workstation, add the /tmp/istio-1.19.3/bin directory to your environment path variable with: export PATH="$PATH:/tmp/istio-1.19.3/bin" Begin the Istio pre-installation check by running: istioctl x precheck Need more information? Visit https://istio.io/latest/docs/setup/install/ $ tree -L 3 . ├── istio-1.19.3 │ ├── bin │ │ └── istioctl │ ├── LICENSE │ ├── manifests │ │ ├── charts │ │ ├── examples │ │ └── profiles │ ├── manifest.yaml │ ├── README.md │ ├── samples │ │ ├── addons │ │ ├── bookinfo │ │ ├── certs │ │ ├── cicd │ │ ├── custom-bootstrap │ │ ├── extauthz │ │ ├── external │ │ ├── grpc-echo │ │ ├── health-check │ │ ├── helloworld │ │ ├── httpbin │ │ ├── jwt-server │ │ ├── kind-lb │ │ ├── multicluster │ │ ├── open-telemetry │ │ ├── operator │ │ ├── ratelimit │ │ ├── README.md │ │ ├── security │ │ ├── sleep │ │ ├── tcp-echo │ │ ├── wasm_modules │ │ └── websockets │ └── tools │ ├── certs │ ├── _istioctl │ └── istioctl.bash - istioctl: change into the Istio package directory and add the
istioctlclient to the PATH environment variable.$ cd istio-* $ export PATH=$PWD/bin:$PATH $ istioctl version client version: 1.19.3 control plane version: 1.19.3 data plane version: 1.19.3 (2 proxies)
- install Istio: To install Istio with a demo profile, execute the following command:
$ istioctl install --set profile=demo This will install the Istio 1.19.3 "demo" profile (with components: Istio core, Istiod, Ingress gateways, and Egress gateways) into the cluster. Proceed? (y/N) y ✔ Istio core installed ✔ Istiod installed ✔ Egress gateways installed ✔ Ingress gateways installed ✔ Installation completeMade this installation the default for injection and validation. $ kubectl get all -n istio-system NAME READY STATUS RESTARTS AGE pod/istio-egressgateway-556f6f58f4-gw9lt 1/1 Running 0 96s pod/istio-ingressgateway-9c8b9b586-q5xrf 1/1 Running 0 96s pod/istiod-644f5d55fc-7h7dw 1/1 Running 0 104s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/istio-egressgateway ClusterIP 10.111.167.27 <none> 80/TCP,443/TCP 96s service/istio-ingressgateway LoadBalancer 10.107.143.167 <pending> 15021:32339/TCP,80:31420/TCP,443:31170/TCP,31400:31384/TCP,15443:30706/TCP 96s service/istiod ClusterIP 10.108.104.117 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 104s NAME READY UP-TO-DATE AVAILABLE AGE deployment.apps/istio-egressgateway 1/1 1 1 96s deployment.apps/istio-ingressgateway 1/1 1 1 96s deployment.apps/istiod 1/1 1 1 104s NAME DESIRED CURRENT READY AGE replicaset.apps/istio-egressgateway-556f6f58f4 1 1 1 96s replicaset.apps/istio-ingressgateway-9c8b9b586 1 1 1 96s replicaset.apps/istiod-644f5d55fc 1 1 1 104s
Ref: Bookinfo Application.
This example deploys a sample application composed of four separate microservices used to demonstrate various Istio features.
The Bookinfo application is broken into four separate microservices:
- productpage: The productpage microservice calls the details and reviews microservices to populate the page.
- details: The details microservice contains book information.
- reviews: The reviews microservice contains book reviews. It also calls the ratings microservice.
- ratings: The ratings microservice contains book ranking information that accompanies a book review.
To run the sample with Istio requires no changes to the application itself. Instead, we simply need to configure and run the services in an Istio-enabled environment, with Envoy sidecars injected along side each service.
Here are the step of deploying the bookinfo application:
- automatic sidecar injection: The default Istio installation uses automatic sidecar injection. If it is not set then
label the namespace that will host the application with
kubectl label namespace default istio-injection=enabled:$ kubectl get namespace default --show-labels NAME STATUS AGE LABELS default Active 28m kubernetes.io/metadata.name=default $ kubectl label namespace default istio-injection=enabled namespace/default labeled $ kubectl get namespace default --show-labels NAME STATUS AGE LABELS default Active 32m istio-injection=enabled,kubernetes.io/metadata.name=default
- Deploy Bookinfo on EC2: Connect to the EC2 instance and deploy the Bookinfo application:
$ cd istio-1.19.3 $ kubectl apply -f samples/bookinfo/platform/kube/bookinfo.yaml service/details created serviceaccount/bookinfo-details created deployment.apps/details-v1 created service/ratings created serviceaccount/bookinfo-ratings created deployment.apps/ratings-v1 created service/reviews created serviceaccount/bookinfo-reviews created deployment.apps/reviews-v1 created deployment.apps/reviews-v2 created deployment.apps/reviews-v3 created service/productpage created serviceaccount/bookinfo-productpage created deployment.apps/productpage-v1 created
The command launches all four services shown in the bookinfo application architecture diagram. All 3 versions of the reviews service, v1, v2, and v3, are started. - Confirm all services and pods are correctly defined and running:
$ kubectl get svc NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE details ClusterIP 10.102.150.210 <none> 9080/TCP 2m41s kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 39m productpage ClusterIP 10.105.65.67 <none> 9080/TCP 2m41s ratings ClusterIP 10.100.98.166 <none> 9080/TCP 2m41s reviews ClusterIP 10.111.86.180 <none> 9080/TCP 2m41s $ kubectl get po NAME READY STATUS RESTARTS AGE details-v1-5f4d584748-gmqf4 1/1 Running 0 3m53s productpage-v1-564d4686f-wbtmm 1/1 Running 0 3m53s ratings-v1-686ccfb5d8-bq47g 1/1 Running 0 3m53s reviews-v1-86896b7648-rtv94 1/1 Running 0 3m53s reviews-v2-b7dcd98fb-cfbmv 1/1 Running 0 3m53s reviews-v3-5c5cc7b6d-sxrdl 1/1 Running 0 3m53s
- Verify everything is working correctly up to this point.
Run this command to see if the app is running inside the cluster and serving HTML pages
by checking for the page title in the response:
$ kubectl exec "$(kubectl get pod -l app=ratings \ -o jsonpath='{.items[0].metadata.name}')" \ -c ratings -- curl -sS productpage:9080/productpage | \ grep -o "<title>.*</title>"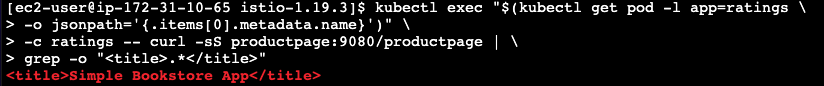
The components deployed on the service mesh by default are not exposed outside the cluster. An Ingress Gateway is deployed as a Kubernetes service of type LoadBalancer (or NodePort). To make Bookinfo accessible external to the cluster, we need to make the application accessible from outside of our Kubernetes cluster, e.g., from a browser. A gateway is used for this purpose.
- Create an Istio Gateway for the Bookinfo application:
$ kubectl apply -f samples/bookinfo/networking/bookinfo-gateway.yaml gateway.networking.istio.io/bookinfo-gateway created virtualservice.networking.istio.io/bookinfo created
Confirm the gateway has been created:$ kubectl get gateway NAME AGE bookinfo-gateway 73s
- Determining the ingress IP and ports:
Set the following environment variables to the name and namespace where the Istio ingress gateway is located in the cluster:
$ export INGRESS_NAME=istio-ingressgateway $ export INGRESS_NS=istio-system
Run the following command to determine if our Kubernetes cluster is in an environment that supports external load balancers:$ kubectl get svc "$INGRESS_NAME" -n "$INGRESS_NS" NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE istio-ingressgateway LoadBalancer 10.107.143.167 10.107.143.167 15021:32339/TCP,80:31420/TCP,443:31170/TCP,31400:31384/TCP,15443:30706/TCP 34m
If the EXTERNAL-IP value is set, our environment has an external load balancer that we can use for the ingress gateway. - set the ingress IP and ports:
$ export INGRESS_HOST=$(kubectl -n "$INGRESS_NS" get service "$INGRESS_NAME" -o jsonpath='{.status.loadBalancer.ingress[0].ip}') $ export INGRESS_PORT=$(kubectl -n "$INGRESS_NS" get service "$INGRESS_NAME" -o jsonpath='{.spec.ports[?(@.name=="http2")].port}') $ export SECURE_INGRESS_PORT=$(kubectl -n "$INGRESS_NS" get service "$INGRESS_NAME" -o jsonpath='{.spec.ports[?(@.name=="https")].port}') $ export TCP_INGRESS_PORT=$(kubectl -n "$INGRESS_NS" get service "$INGRESS_NAME" -o jsonpath='{.spec.ports[?(@.name=="tcp")].port}') - Set
GATEWAY_URL:$ export GATEWAY_URL=$INGRESS_HOST:$INGRESS_PORT $ echo $GATEWAY_URL 10.107.143.167:80
- To confirm that the Bookinfo application is accessible from outside the cluster, run the following
curlcommand:$ curl -s "http://${GATEWAY_URL}/productpage" | grep -o "<title>.*</title>" <title>Simple Bookstore App</title>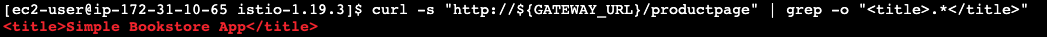 We can also point our browser to
We can also point our browser to http://$GATEWAY_URL/productpageto view the Bookinfo web page. If we refresh the page several times, we should see different versions of reviews shown in productpage, presented in a round robin style (red stars, black stars, no stars), since we haven't yet used Istio to control the version routing.
Docker & K8s
- Docker install on Amazon Linux AMI
- Docker install on EC2 Ubuntu 14.04
- Docker container vs Virtual Machine
- Docker install on Ubuntu 14.04
- Docker Hello World Application
- Nginx image - share/copy files, Dockerfile
- Working with Docker images : brief introduction
- Docker image and container via docker commands (search, pull, run, ps, restart, attach, and rm)
- More on docker run command (docker run -it, docker run --rm, etc.)
- Docker Networks - Bridge Driver Network
- Docker Persistent Storage
- File sharing between host and container (docker run -d -p -v)
- Linking containers and volume for datastore
- Dockerfile - Build Docker images automatically I - FROM, MAINTAINER, and build context
- Dockerfile - Build Docker images automatically II - revisiting FROM, MAINTAINER, build context, and caching
- Dockerfile - Build Docker images automatically III - RUN
- Dockerfile - Build Docker images automatically IV - CMD
- Dockerfile - Build Docker images automatically V - WORKDIR, ENV, ADD, and ENTRYPOINT
- Docker - Apache Tomcat
- Docker - NodeJS
- Docker - NodeJS with hostname
- Docker Compose - NodeJS with MongoDB
- Docker - Prometheus and Grafana with Docker-compose
- Docker - StatsD/Graphite/Grafana
- Docker - Deploying a Java EE JBoss/WildFly Application on AWS Elastic Beanstalk Using Docker Containers
- Docker : NodeJS with GCP Kubernetes Engine
- Docker : Jenkins Multibranch Pipeline with Jenkinsfile and Github
- Docker : Jenkins Master and Slave
- Docker - ELK : ElasticSearch, Logstash, and Kibana
- Docker - ELK 7.6 : Elasticsearch on Centos 7
- Docker - ELK 7.6 : Filebeat on Centos 7
- Docker - ELK 7.6 : Logstash on Centos 7
- Docker - ELK 7.6 : Kibana on Centos 7
- Docker - ELK 7.6 : Elastic Stack with Docker Compose
- Docker - Deploy Elastic Cloud on Kubernetes (ECK) via Elasticsearch operator on minikube
- Docker - Deploy Elastic Stack via Helm on minikube
- Docker Compose - A gentle introduction with WordPress
- Docker Compose - MySQL
- MEAN Stack app on Docker containers : micro services
- MEAN Stack app on Docker containers : micro services via docker-compose
- Docker Compose - Hashicorp's Vault and Consul Part A (install vault, unsealing, static secrets, and policies)
- Docker Compose - Hashicorp's Vault and Consul Part B (EaaS, dynamic secrets, leases, and revocation)
- Docker Compose - Hashicorp's Vault and Consul Part C (Consul)
- Docker Compose with two containers - Flask REST API service container and an Apache server container
- Docker compose : Nginx reverse proxy with multiple containers
- Docker & Kubernetes : Envoy - Getting started
- Docker & Kubernetes : Envoy - Front Proxy
- Docker & Kubernetes : Ambassador - Envoy API Gateway on Kubernetes
- Docker Packer
- Docker Cheat Sheet
- Docker Q & A #1
- Kubernetes Q & A - Part I
- Kubernetes Q & A - Part II
- Docker - Run a React app in a docker
- Docker - Run a React app in a docker II (snapshot app with nginx)
- Docker - NodeJS and MySQL app with React in a docker
- Docker - Step by Step NodeJS and MySQL app with React - I
- Installing LAMP via puppet on Docker
- Docker install via Puppet
- Nginx Docker install via Ansible
- Apache Hadoop CDH 5.8 Install with QuickStarts Docker
- Docker - Deploying Flask app to ECS
- Docker Compose - Deploying WordPress to AWS
- Docker - WordPress Deploy to ECS with Docker-Compose (ECS-CLI EC2 type)
- Docker - WordPress Deploy to ECS with Docker-Compose (ECS-CLI Fargate type)
- Docker - ECS Fargate
- Docker - AWS ECS service discovery with Flask and Redis
- Docker & Kubernetes : minikube
- Docker & Kubernetes 2 : minikube Django with Postgres - persistent volume
- Docker & Kubernetes 3 : minikube Django with Redis and Celery
- Docker & Kubernetes 4 : Django with RDS via AWS Kops
- Docker & Kubernetes : Kops on AWS
- Docker & Kubernetes : Ingress controller on AWS with Kops
- Docker & Kubernetes : HashiCorp's Vault and Consul on minikube
- Docker & Kubernetes : HashiCorp's Vault and Consul - Auto-unseal using Transit Secrets Engine
- Docker & Kubernetes : Persistent Volumes & Persistent Volumes Claims - hostPath and annotations
- Docker & Kubernetes : Persistent Volumes - Dynamic volume provisioning
- Docker & Kubernetes : DaemonSet
- Docker & Kubernetes : Secrets
- Docker & Kubernetes : kubectl command
- Docker & Kubernetes : Assign a Kubernetes Pod to a particular node in a Kubernetes cluster
- Docker & Kubernetes : Configure a Pod to Use a ConfigMap
- AWS : EKS (Elastic Container Service for Kubernetes)
- Docker & Kubernetes : Run a React app in a minikube
- Docker & Kubernetes : Minikube install on AWS EC2
- Docker & Kubernetes : Cassandra with a StatefulSet
- Docker & Kubernetes : Terraform and AWS EKS
- Docker & Kubernetes : Pods and Service definitions
- Docker & Kubernetes : Service IP and the Service Type
- Docker & Kubernetes : Kubernetes DNS with Pods and Services
- Docker & Kubernetes : Headless service and discovering pods
- Docker & Kubernetes : Scaling and Updating application
- Docker & Kubernetes : Horizontal pod autoscaler on minikubes
- Docker & Kubernetes : From a monolithic app to micro services on GCP Kubernetes
- Docker & Kubernetes : Rolling updates
- Docker & Kubernetes : Deployments to GKE (Rolling update, Canary and Blue-green deployments)
- Docker & Kubernetes : Slack Chat Bot with NodeJS on GCP Kubernetes
- Docker & Kubernetes : Continuous Delivery with Jenkins Multibranch Pipeline for Dev, Canary, and Production Environments on GCP Kubernetes
- Docker & Kubernetes : NodePort vs LoadBalancer vs Ingress
- Docker & Kubernetes : MongoDB / MongoExpress on Minikube
- Docker & Kubernetes : Load Testing with Locust on GCP Kubernetes
- Docker & Kubernetes : MongoDB with StatefulSets on GCP Kubernetes Engine
- Docker & Kubernetes : Nginx Ingress Controller on Minikube
- Docker & Kubernetes : Setting up Ingress with NGINX Controller on Minikube (Mac)
- Docker & Kubernetes : Nginx Ingress Controller for Dashboard service on Minikube
- Docker & Kubernetes : Nginx Ingress Controller on GCP Kubernetes
- Docker & Kubernetes : Kubernetes Ingress with AWS ALB Ingress Controller in EKS
- Docker & Kubernetes : Setting up a private cluster on GCP Kubernetes
- Docker & Kubernetes : Kubernetes Namespaces (default, kube-public, kube-system) and switching namespaces (kubens)
- Docker & Kubernetes : StatefulSets on minikube
- Docker & Kubernetes : RBAC
- Docker & Kubernetes Service Account, RBAC, and IAM
- Docker & Kubernetes - Kubernetes Service Account, RBAC, IAM with EKS ALB, Part 1
- Docker & Kubernetes : Helm Chart
- Docker & Kubernetes : My first Helm deploy
- Docker & Kubernetes : Readiness and Liveness Probes
- Docker & Kubernetes : Helm chart repository with Github pages
- Docker & Kubernetes : Deploying WordPress and MariaDB with Ingress to Minikube using Helm Chart
- Docker & Kubernetes : Deploying WordPress and MariaDB to AWS using Helm 2 Chart
- Docker & Kubernetes : Deploying WordPress and MariaDB to AWS using Helm 3 Chart
- Docker & Kubernetes : Helm Chart for Node/Express and MySQL with Ingress
- Docker & Kubernetes : Deploy Prometheus and Grafana using Helm and Prometheus Operator - Monitoring Kubernetes node resources out of the box
- Docker & Kubernetes : Deploy Prometheus and Grafana using kube-prometheus-stack Helm Chart
- Docker & Kubernetes : Istio (service mesh) sidecar proxy on GCP Kubernetes
- Docker & Kubernetes : Istio on EKS
- Docker & Kubernetes : Istio on Minikube with AWS EC2 for Bookinfo Application
- Docker & Kubernetes : Deploying .NET Core app to Kubernetes Engine and configuring its traffic managed by Istio (Part I)
- Docker & Kubernetes : Deploying .NET Core app to Kubernetes Engine and configuring its traffic managed by Istio (Part II - Prometheus, Grafana, pin a service, split traffic, and inject faults)
- Docker & Kubernetes : Helm Package Manager with MySQL on GCP Kubernetes Engine
- Docker & Kubernetes : Deploying Memcached on Kubernetes Engine
- Docker & Kubernetes : EKS Control Plane (API server) Metrics with Prometheus
- Docker & Kubernetes : Spinnaker on EKS with Halyard
- Docker & Kubernetes : Continuous Delivery Pipelines with Spinnaker and Kubernetes Engine
- Docker & Kubernetes : Multi-node Local Kubernetes cluster : Kubeadm-dind (docker-in-docker)
- Docker & Kubernetes : Multi-node Local Kubernetes cluster : Kubeadm-kind (k8s-in-docker)
- Docker & Kubernetes : nodeSelector, nodeAffinity, taints/tolerations, pod affinity and anti-affinity - Assigning Pods to Nodes
- Docker & Kubernetes : Jenkins-X on EKS
- Docker & Kubernetes : ArgoCD App of Apps with Heml on Kubernetes
- Docker & Kubernetes : ArgoCD on Kubernetes cluster
- Docker & Kubernetes : GitOps with ArgoCD for Continuous Delivery to Kubernetes clusters (minikube) - guestbook
Ph.D. / Golden Gate Ave, San Francisco / Seoul National Univ / Carnegie Mellon / UC Berkeley / DevOps / Deep Learning / Visualization